Cisco Tetration - Hands-On Lab
Module24: Policy Enforcement - OpenCart
In this module we will enable enforcement for the OpenCart application. We will review the deployed policies both before and after enabling enforcement to compare the results, and then once in enforcement test access to the application. We will also test the user-based policy as defined in Module 16
Steps for this Module
Step 001 - Navigate to Inventory Search
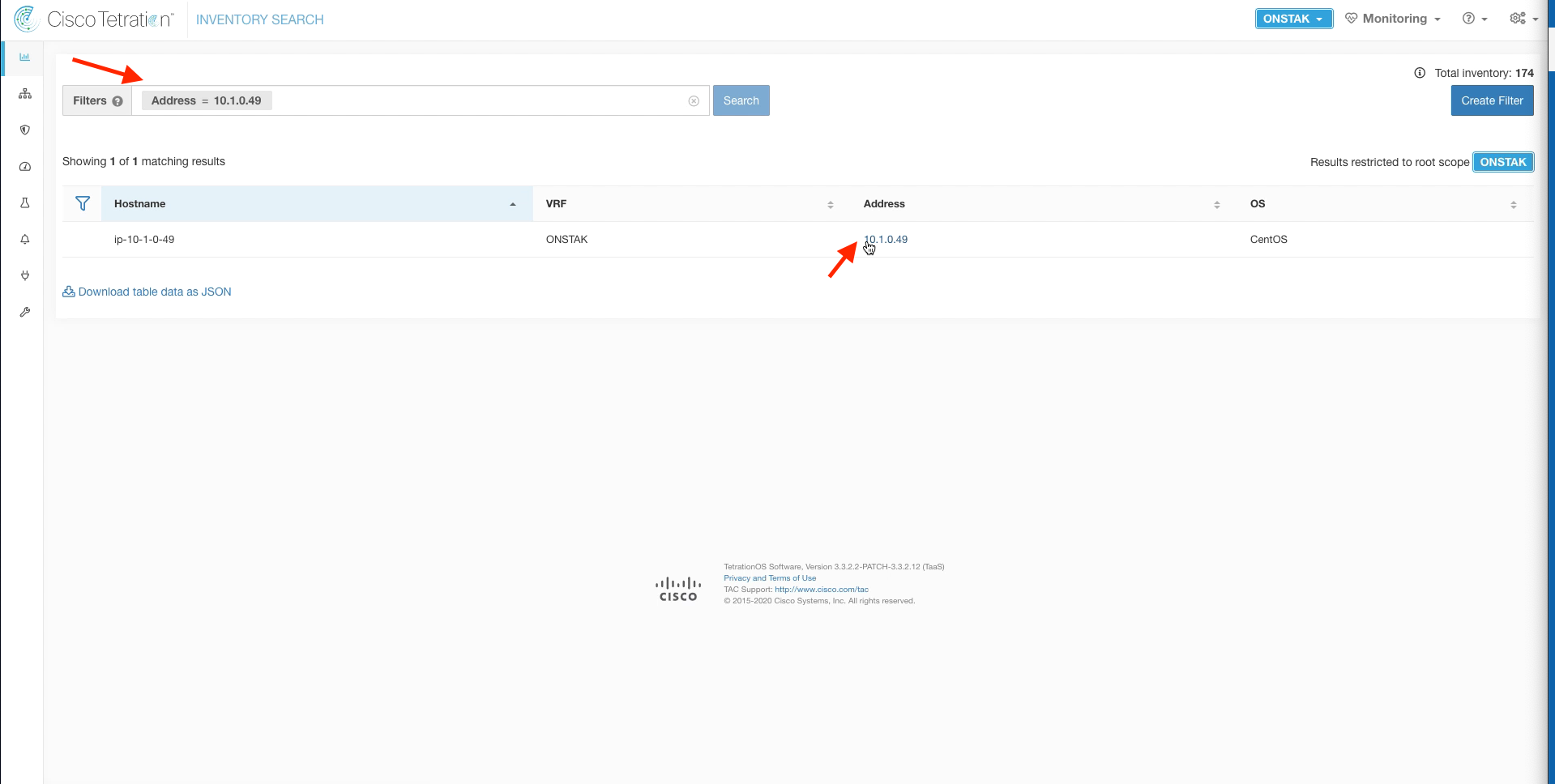
Step 002 - Search for the Apache Linux machine
Step 003 - View the policies on the Apache Linux machine
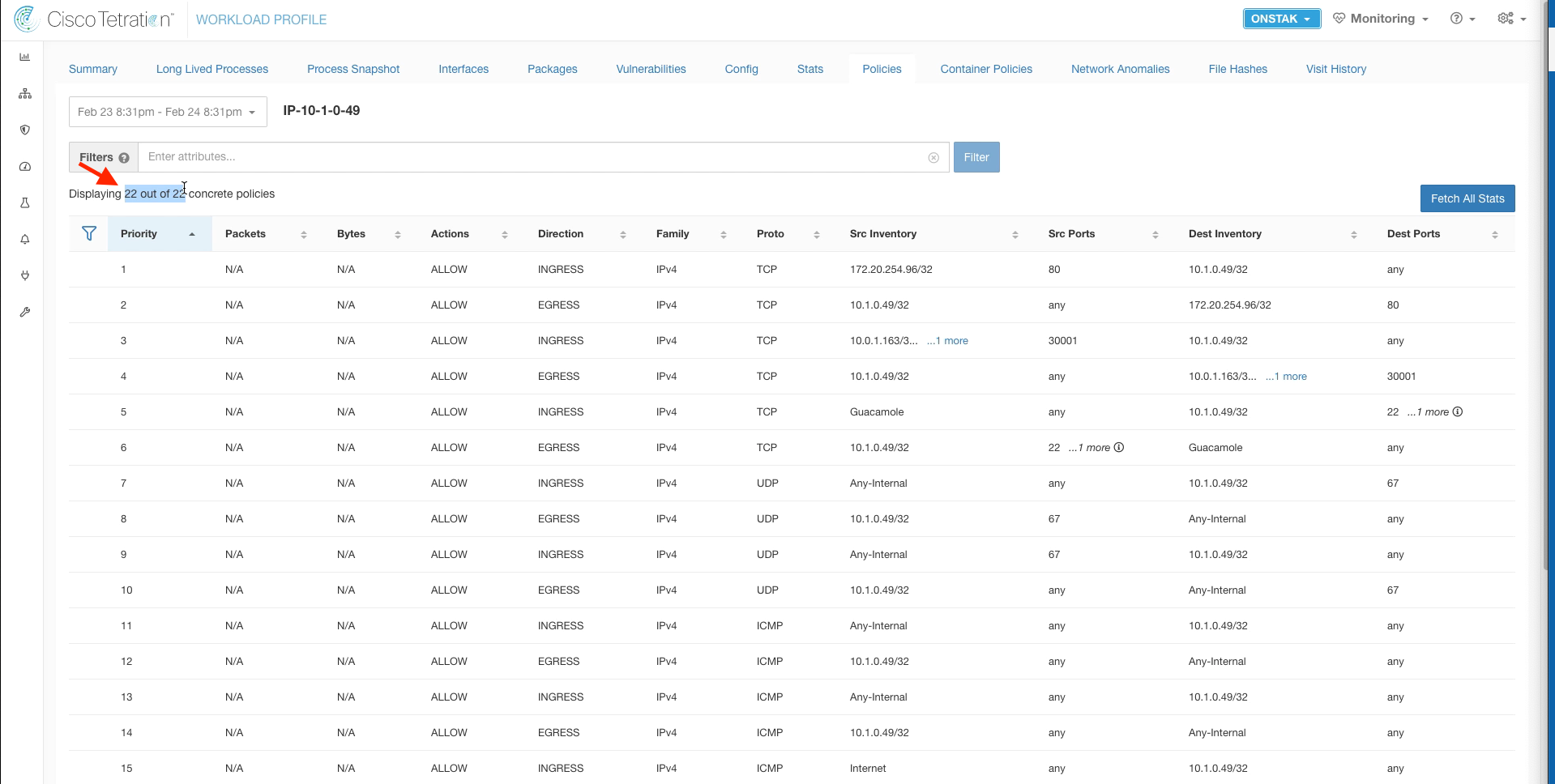
Step 004 - View current number of policies present
Step 005 - Switch to OpenCart application workspace
Step 006 - Begin Enforcement
Step 007 - Enforce the latest published policies
Step 008 - Navigate to Inventory Search
Step 009 - Click on the Apache Linux server
Step 010 - View current Policies
Step 011 - Observe the increased policy rules
Step 012 - Open a session to the Employee Ubuntu desktop
Step 013 - Open a session to the SysAdmin Ubuntu desktop
Step 014 - Open a browser session to the external IP
Step 015 - Connect to the Apache Linux machine from the Employee desktop
Step 016 - Attempt to SSH to the Apache Linux machine from the Employee desktop
Step 017 - Connect to the Apache Linux machine from the SysAdmin desktop
Step 018 - Attempt to SSH to the Apache Linux machine from the SysAdmin desktop
Step 019 - Attempt to SSH to the MySQL machine from the Employee desktop
Step 020 - Open a session to the Kali Linux machine
Step 021 - Attempt to connect to the Apache Linux machine on TCP 8080
Step 022 - Connect to TCP 8080 on the Apache Linux machine from the Employee desktop
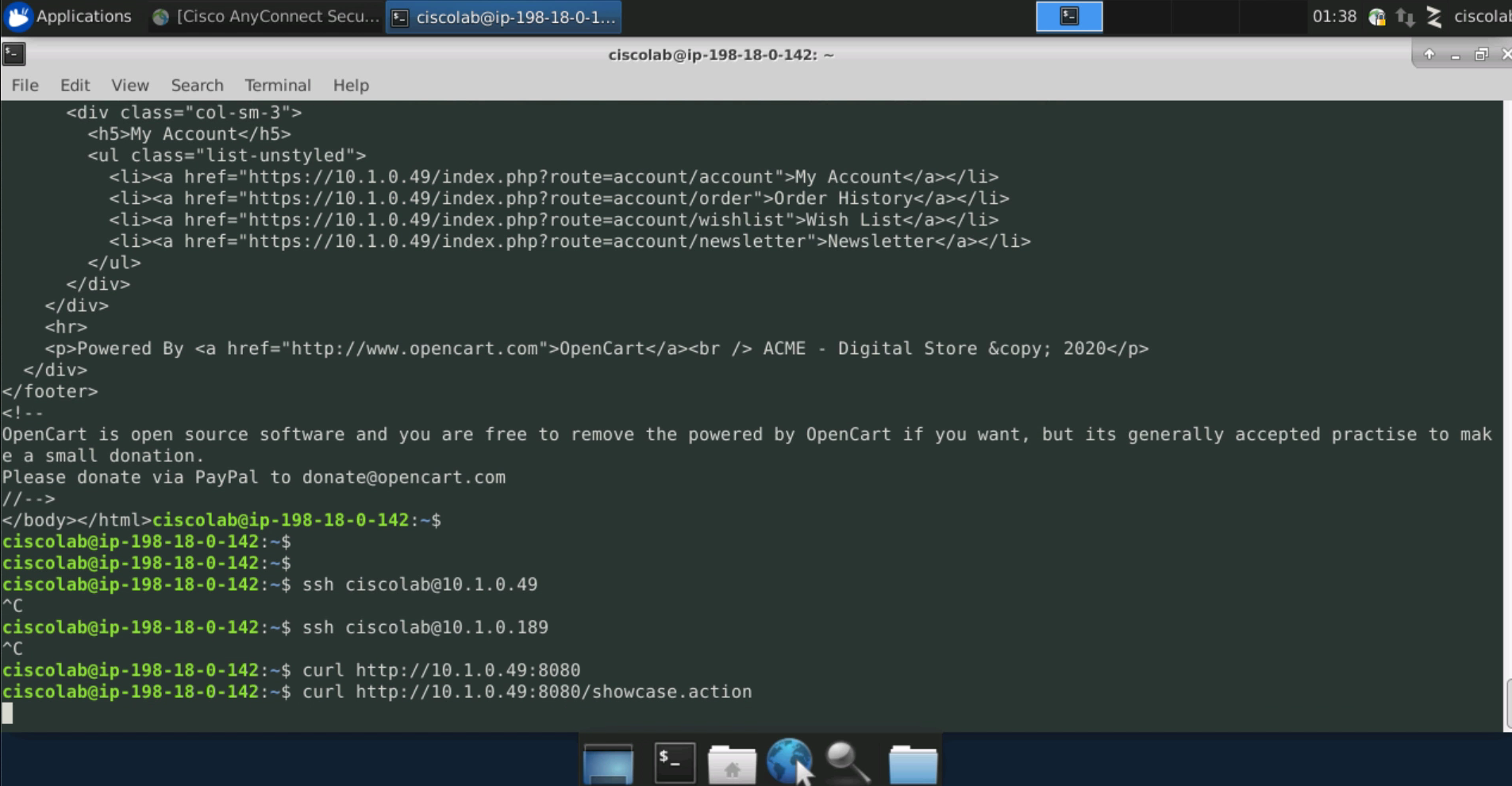
Step 023 - View the curl output from the previous task
Step 024 - Open a session to the nopCommerce IIS server
Step 025 - Attempt a web session to the Apache Linux server
Step 026 - Open a session to the Apache Linux server
Step 027 - Attempt a web session to the IIS web server
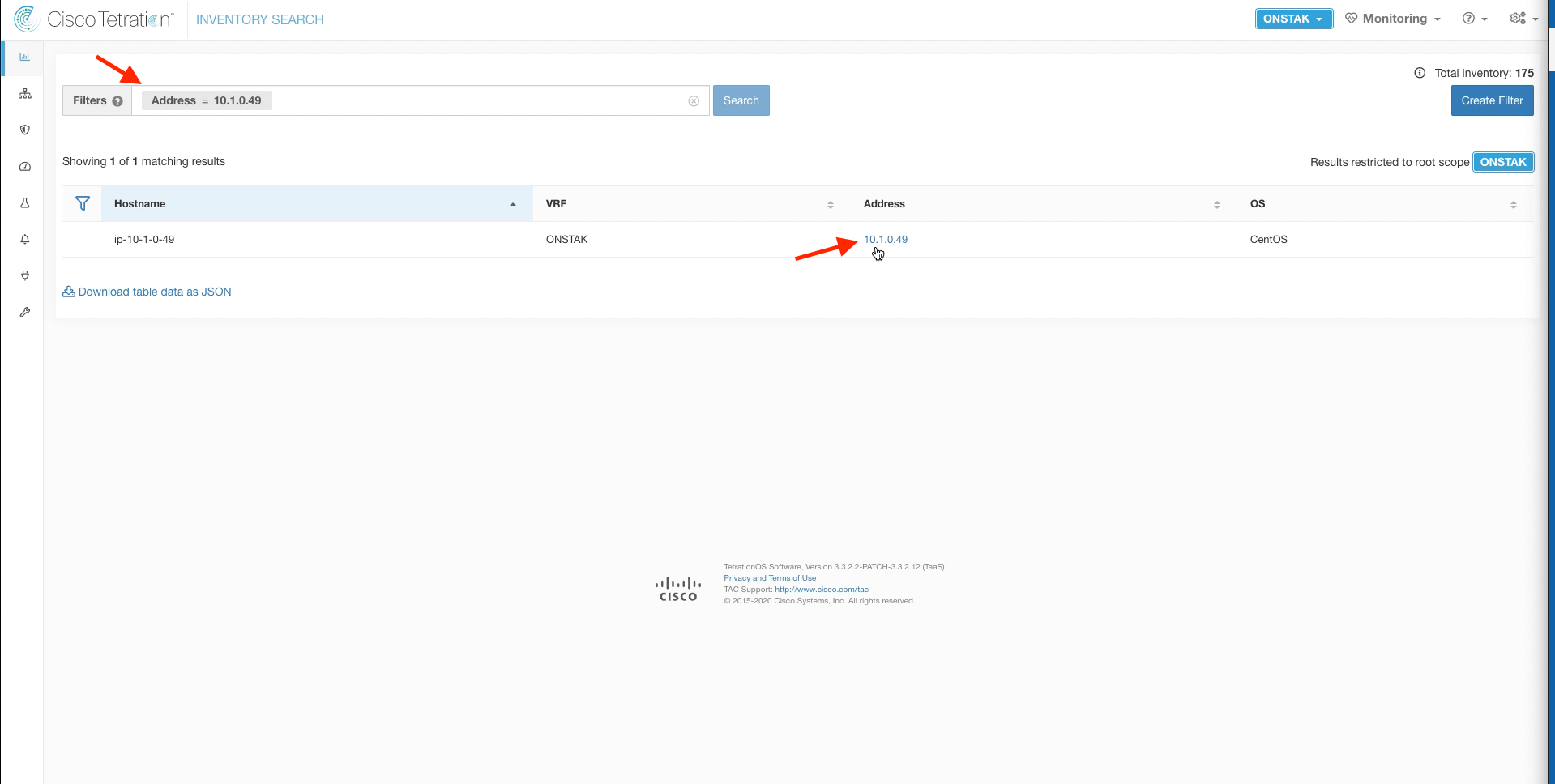
Navigate to Inventory Search.
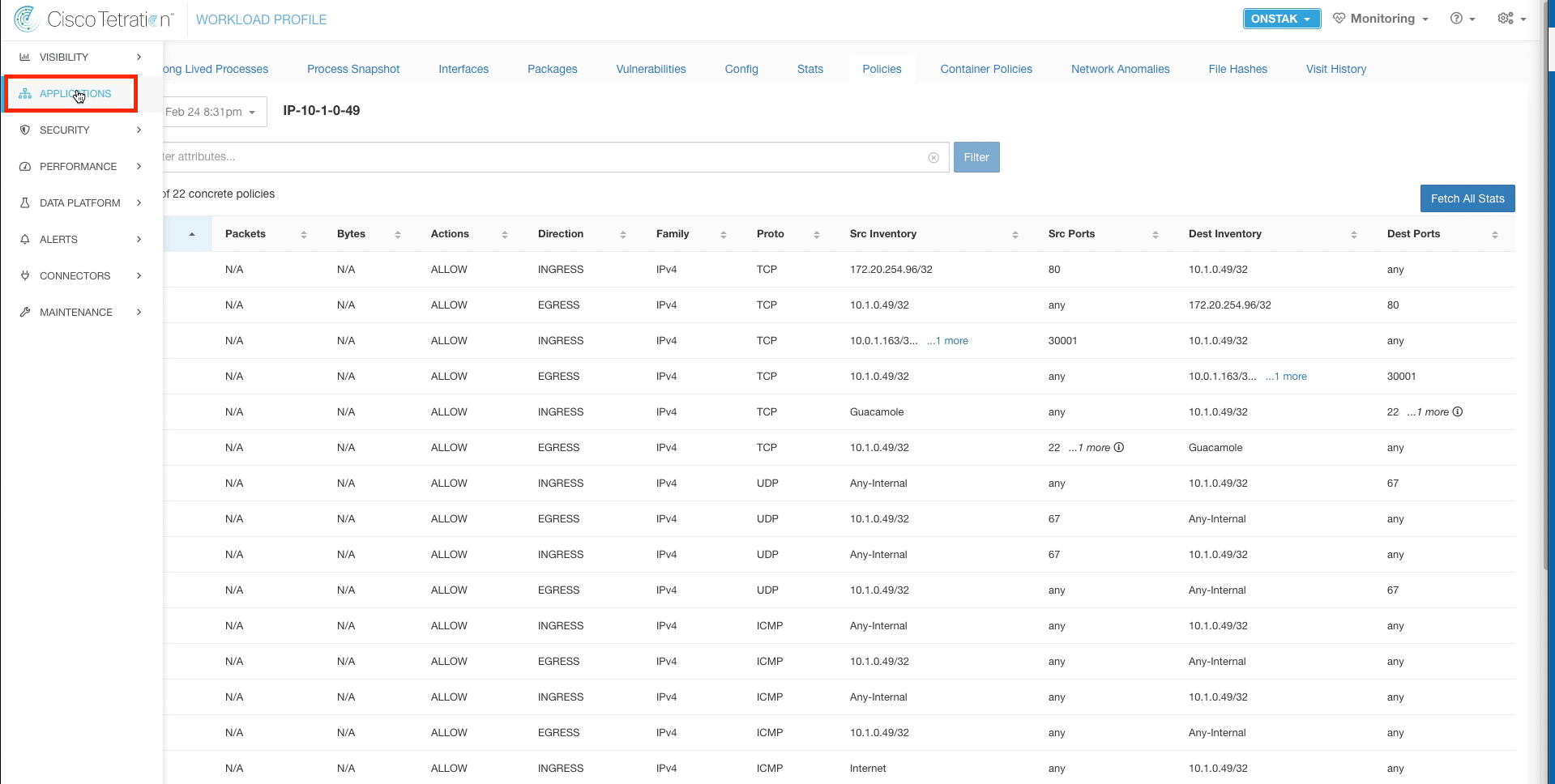
Filter for the IP address of the Apache web server. Then click on the IP address under the Address column.
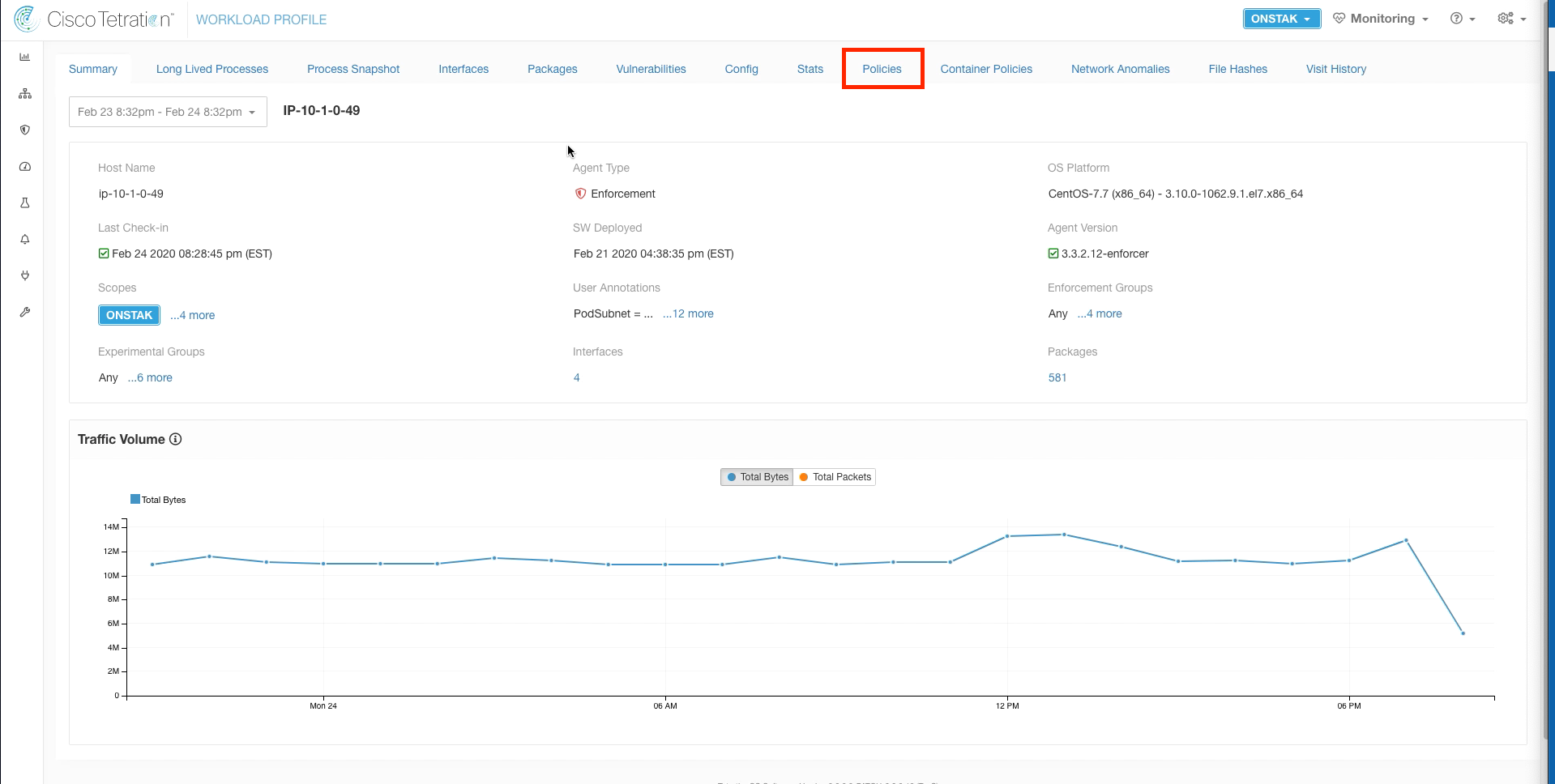
On the Workload Profile, click on Policies.
Notice that there are currently 22 policies present. We will see this increase when we enable enforcement on the OpenCart application workspace.
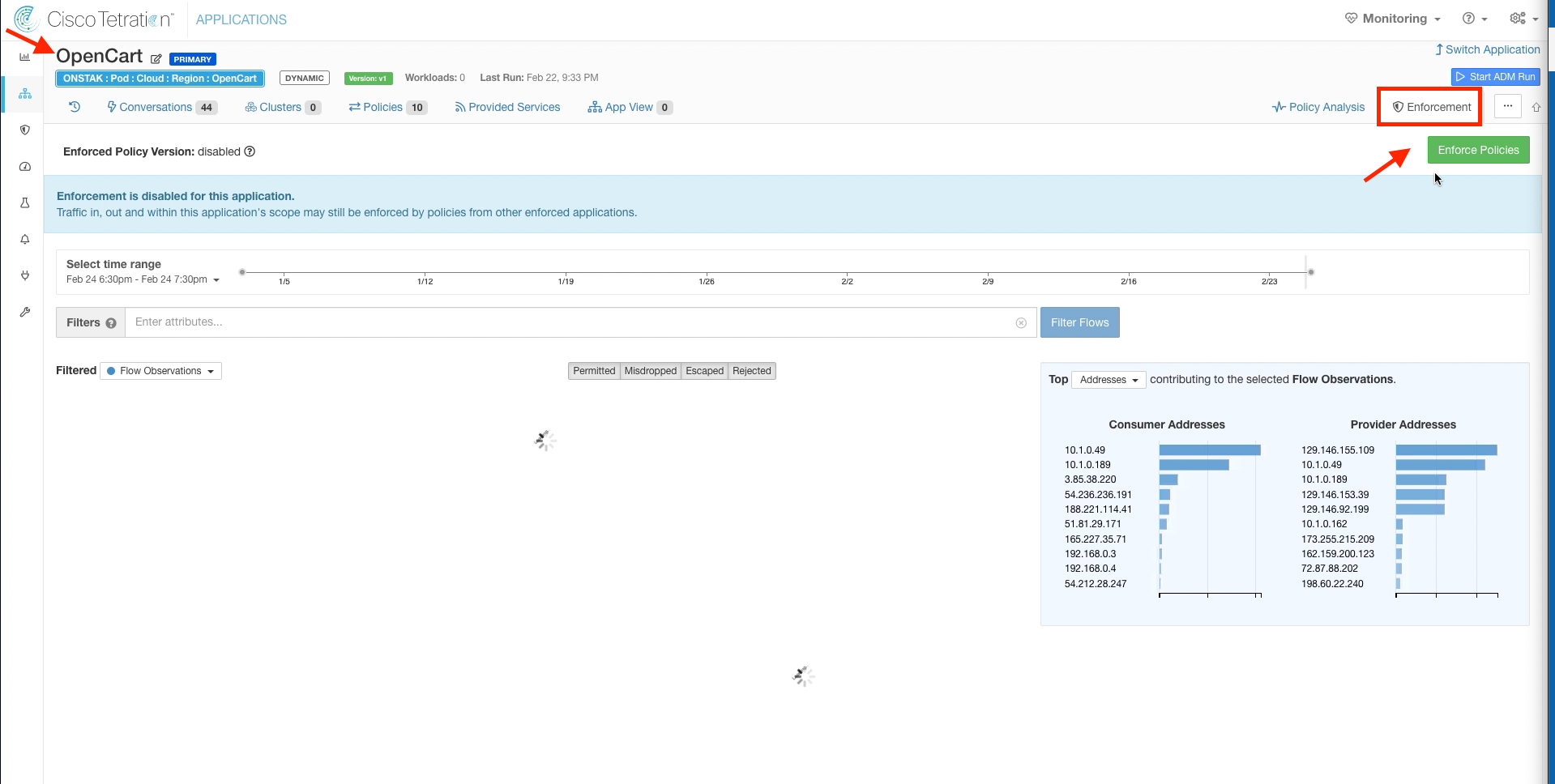
Navigate to Applications and select the OpenCart application workspace.
Click on the Enforcement tab, and select Enforce Policies.
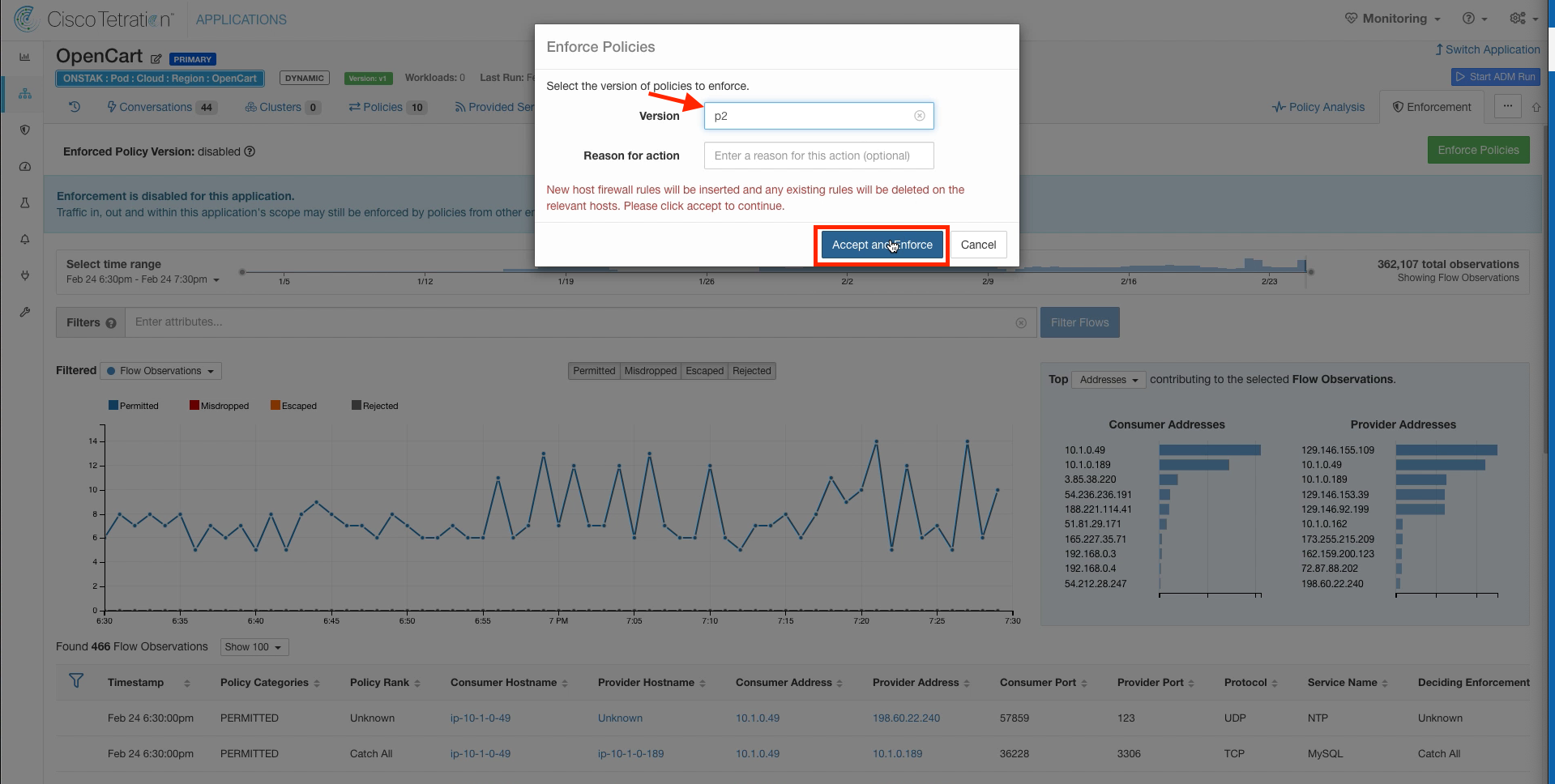
Select the latest version of policy, and then click Accept and Enforce. Optionally, a reason can be entered which will show up in the application event log.
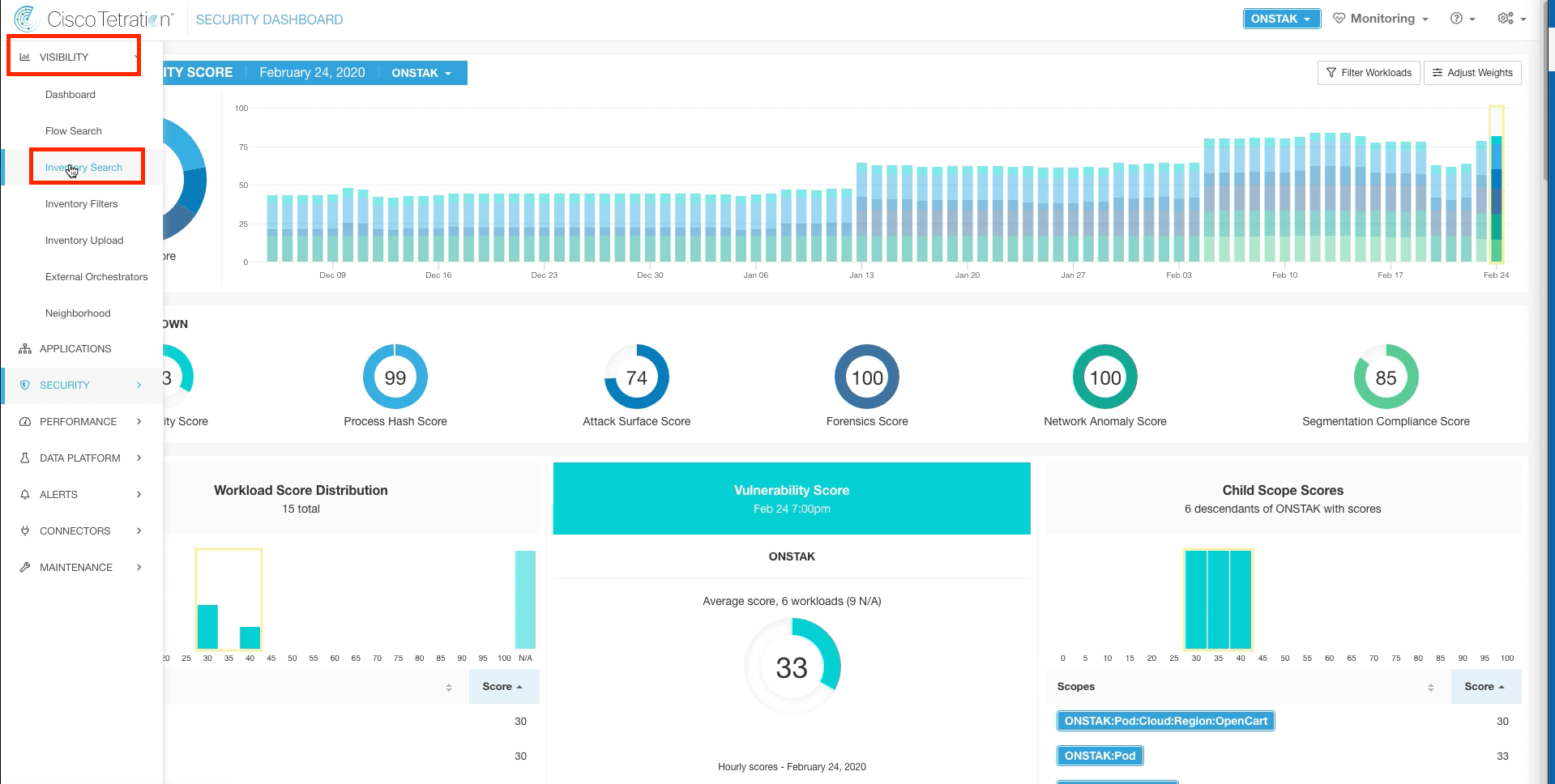
Navigate to Inventory Search.
Search for the IP address of the Apache web server and then click on the IP address.
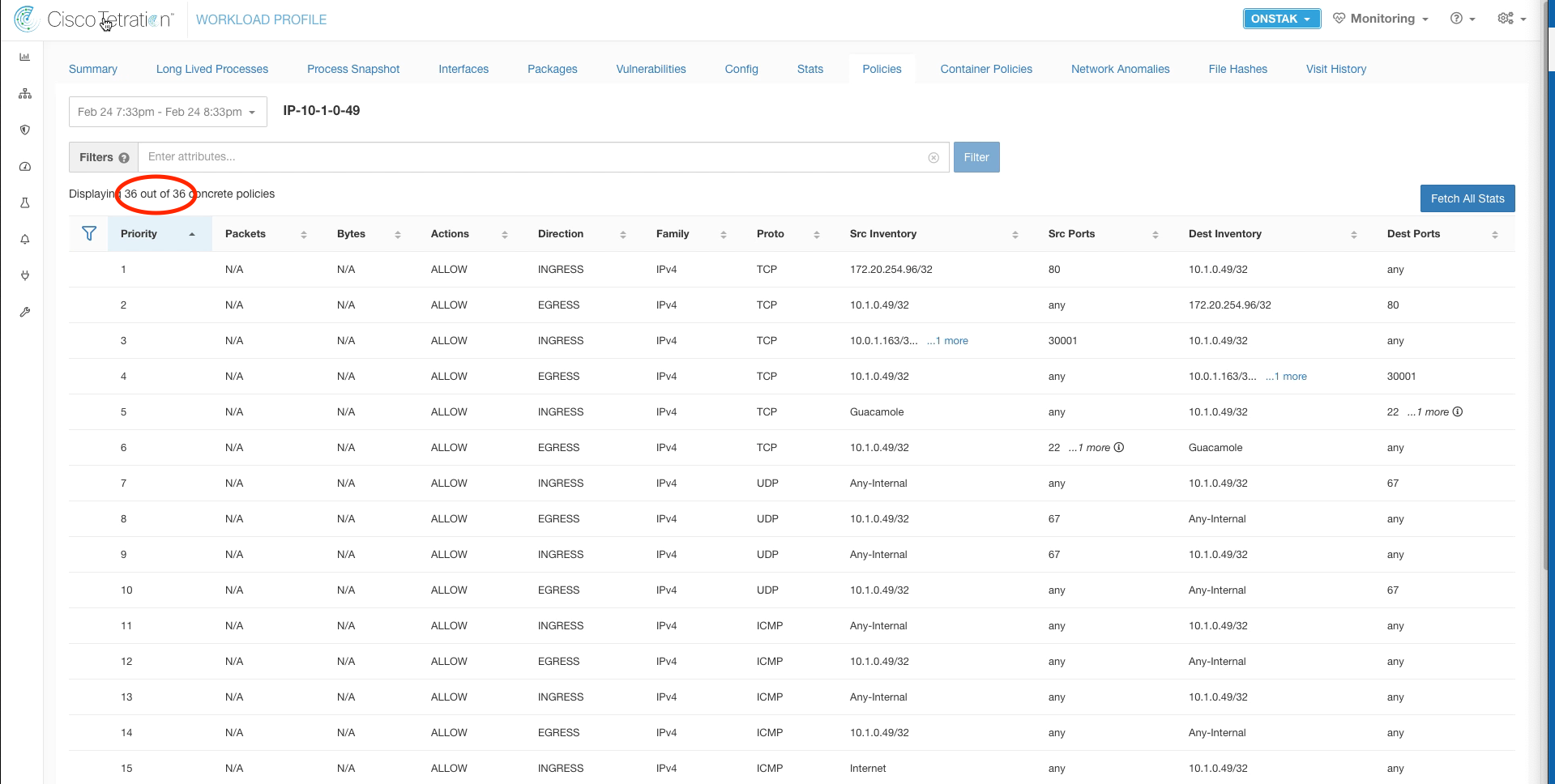
Click on Policies.
Check the number of policies. This number should increase from what we observed previously. It may take a minute for the increased number of policies to be displayed.
Open a session to the Employee desktop.
In a new tab, also open a session to the SysAdmin desktop.
In another tab, test connectivity to the Apace web server public IP address.
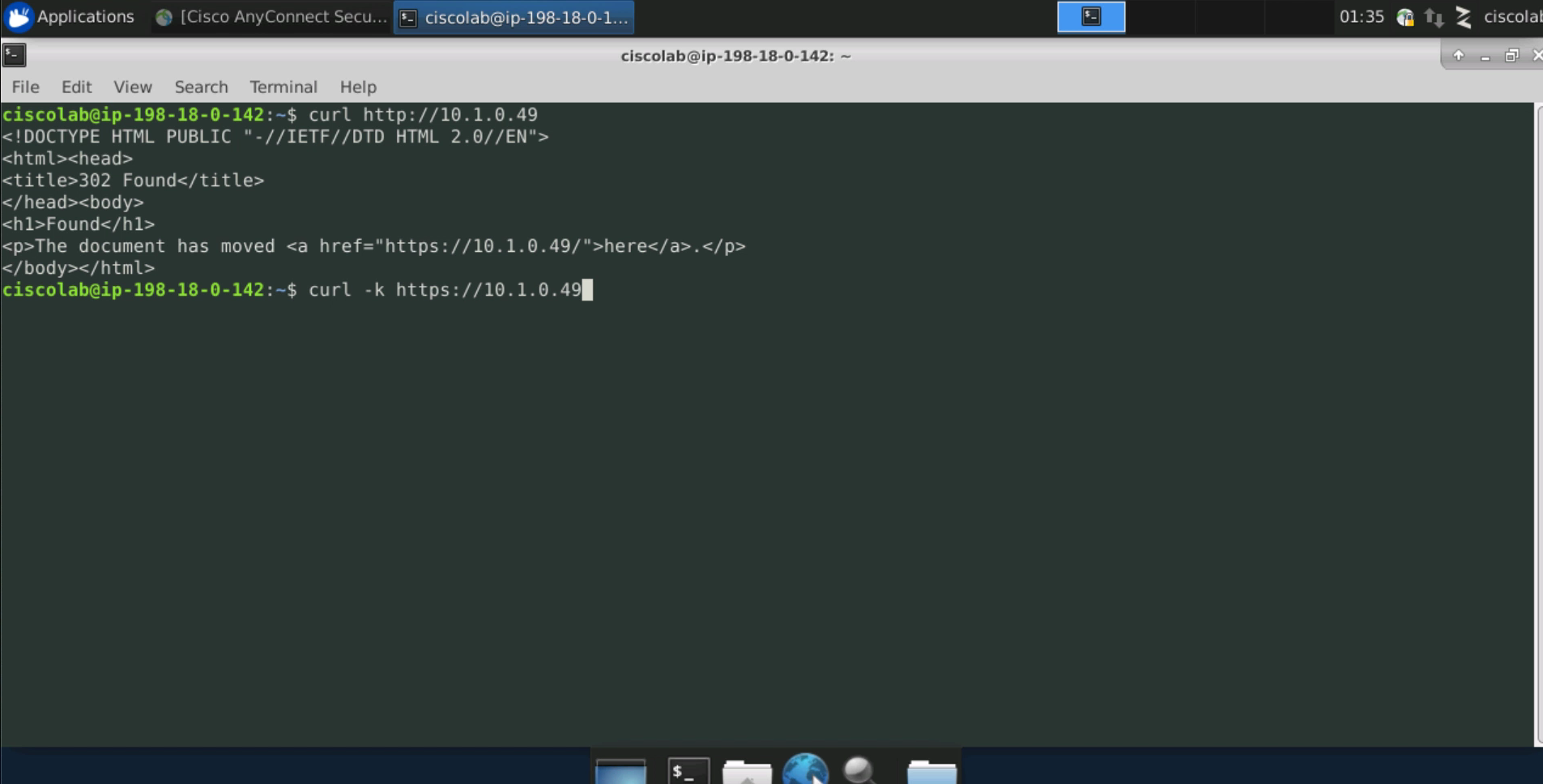
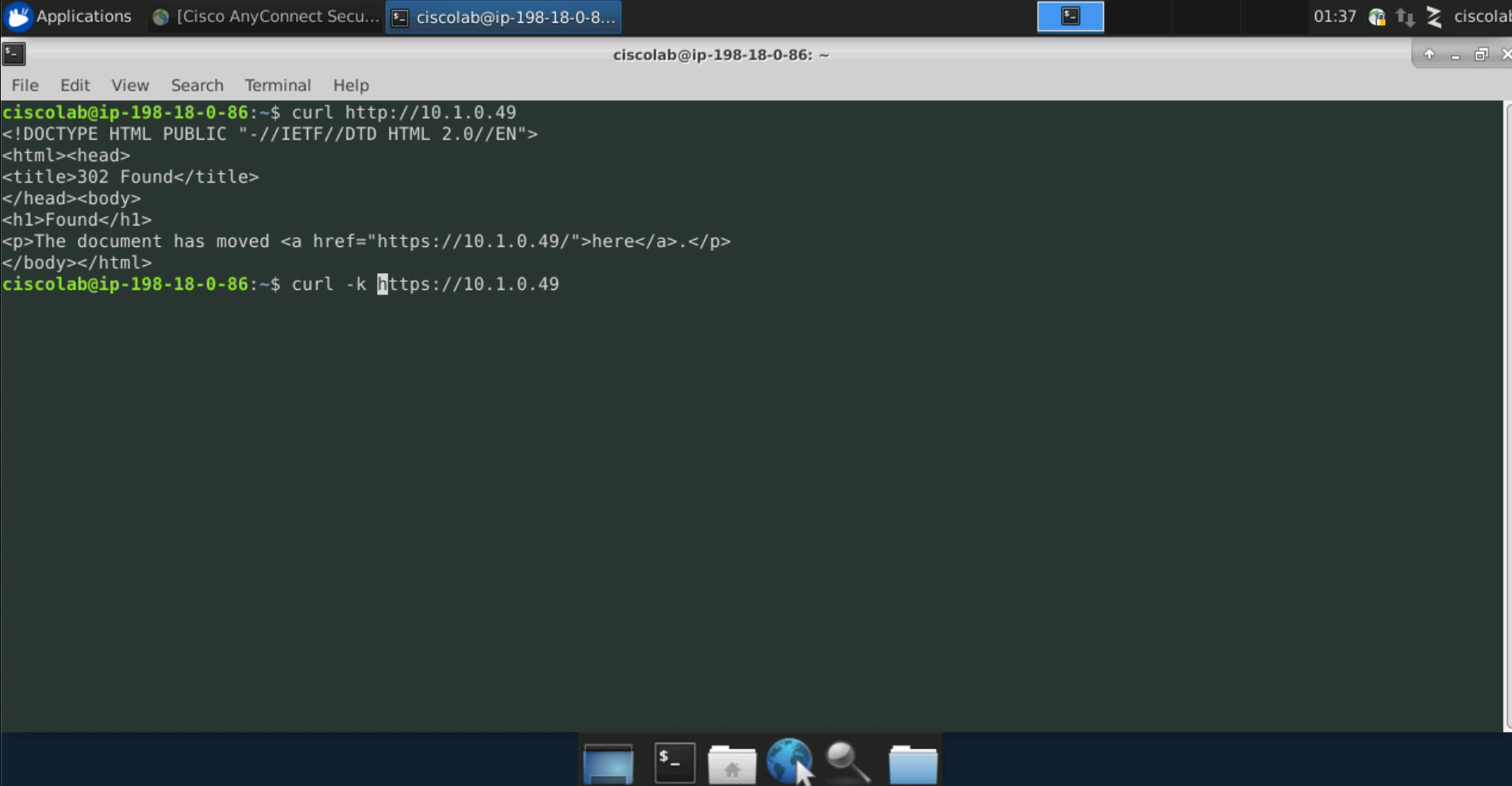
From the Employee desktop, open the Terminal application and use the curl command to attempt an HTTP connection to the IIS web server. The Terminal application can be opened by clicking the black icon on the menu at the bottom middle of the screen. The command should return output indicating “The document has moved”, which indicates that the traffic is getting there on TCP port 80. This is attempting a redirect to SSL. To make the connection with ssl, type curl -k https://<APACHE_WEB_SERVER_IP>. This should return a text representation of the web site.
Attempt an SSH connection to the Apache web server from the Employee desktop. This connection should time out, as SSH is not permitted from Employees to the Apache web server.
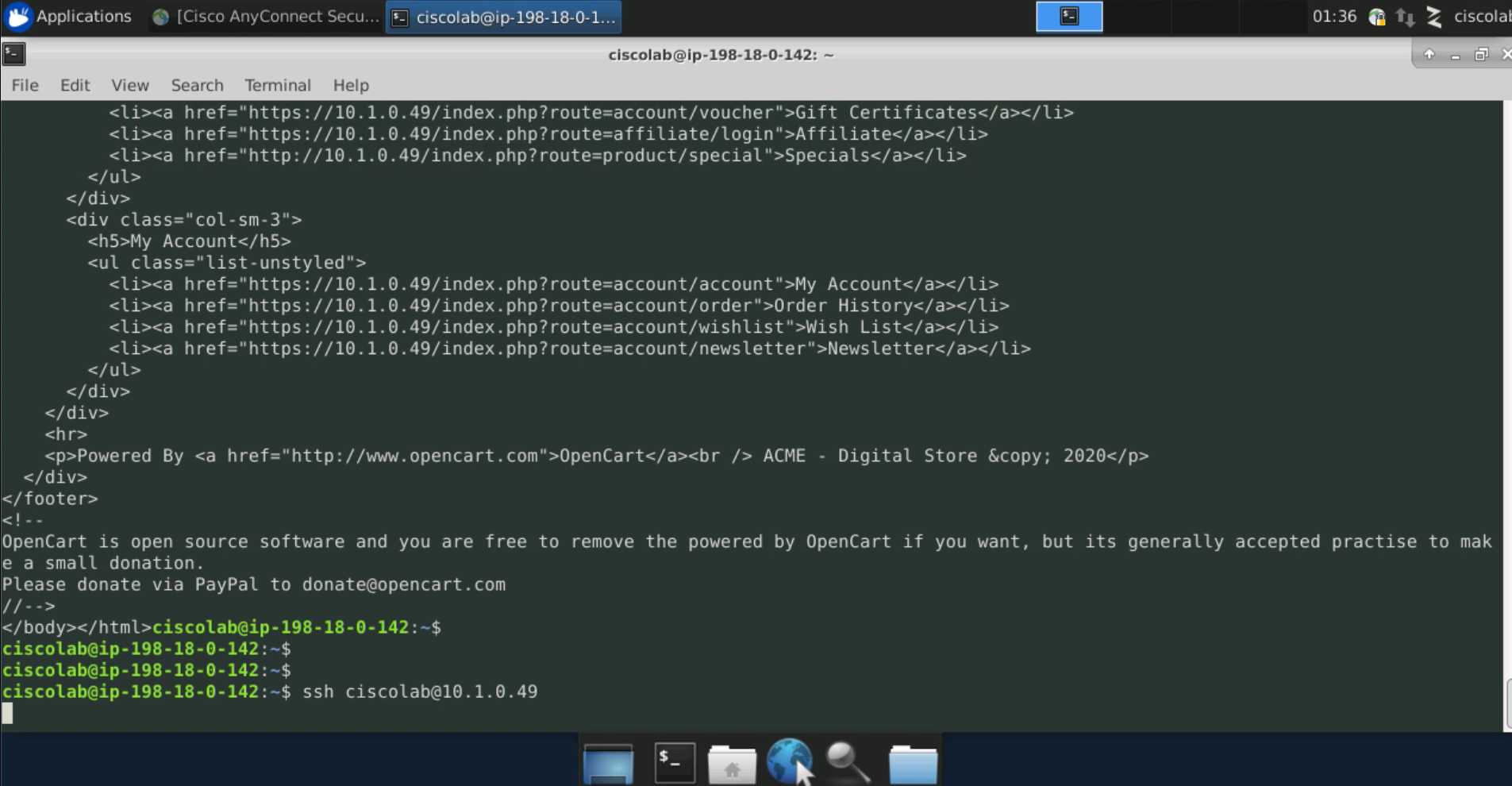
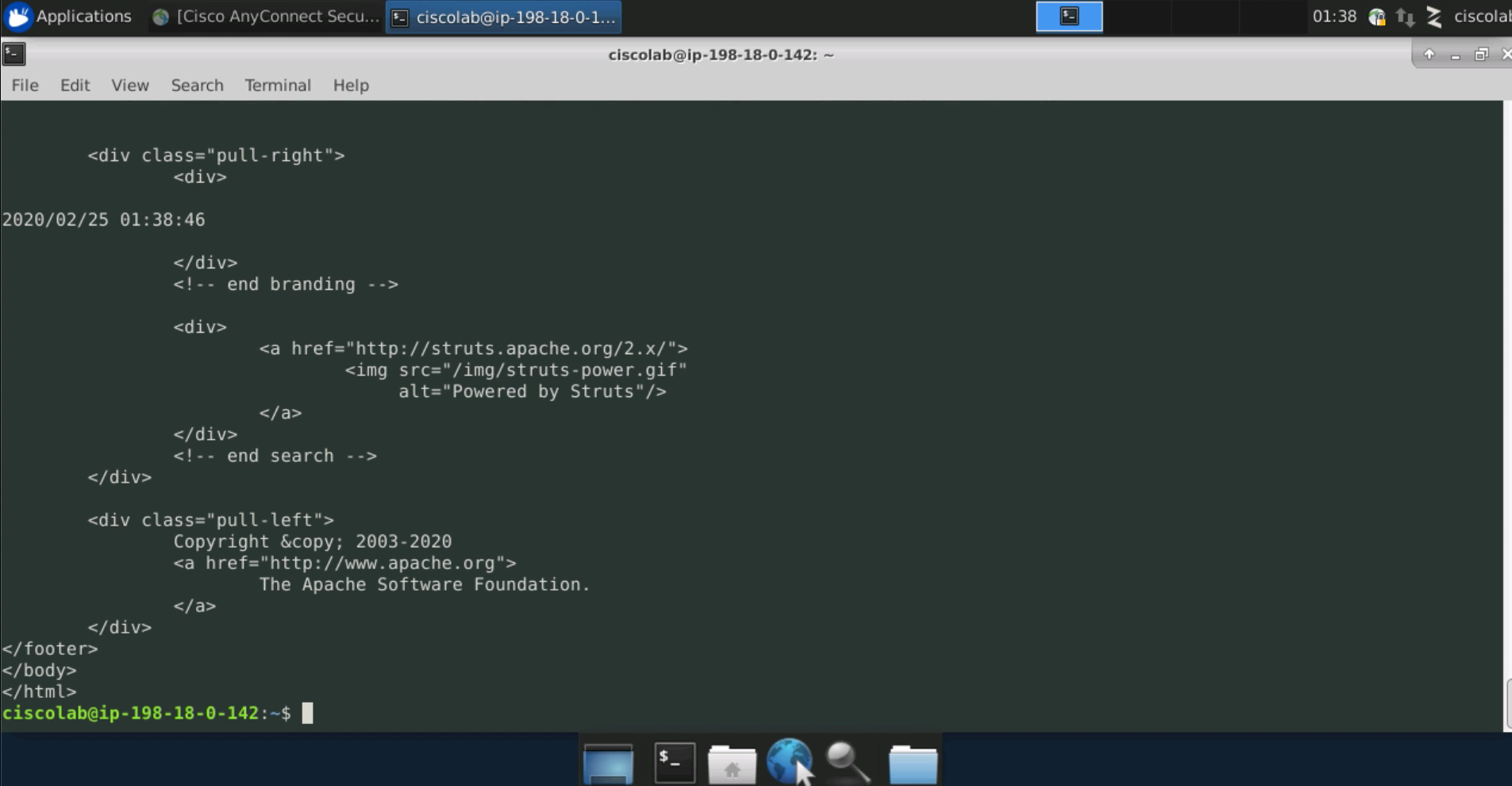
From the SysAdmin desktop, open the Terminal application and attempt an HTTP connection to the Apache web server using the curl command as shown in the image. Output should be returned indicating “The document has moved”. Attempt a connection using SSL with the command curl -k https://<APACHE_WEB_SERVER_IP. The text-based web site should be returned.
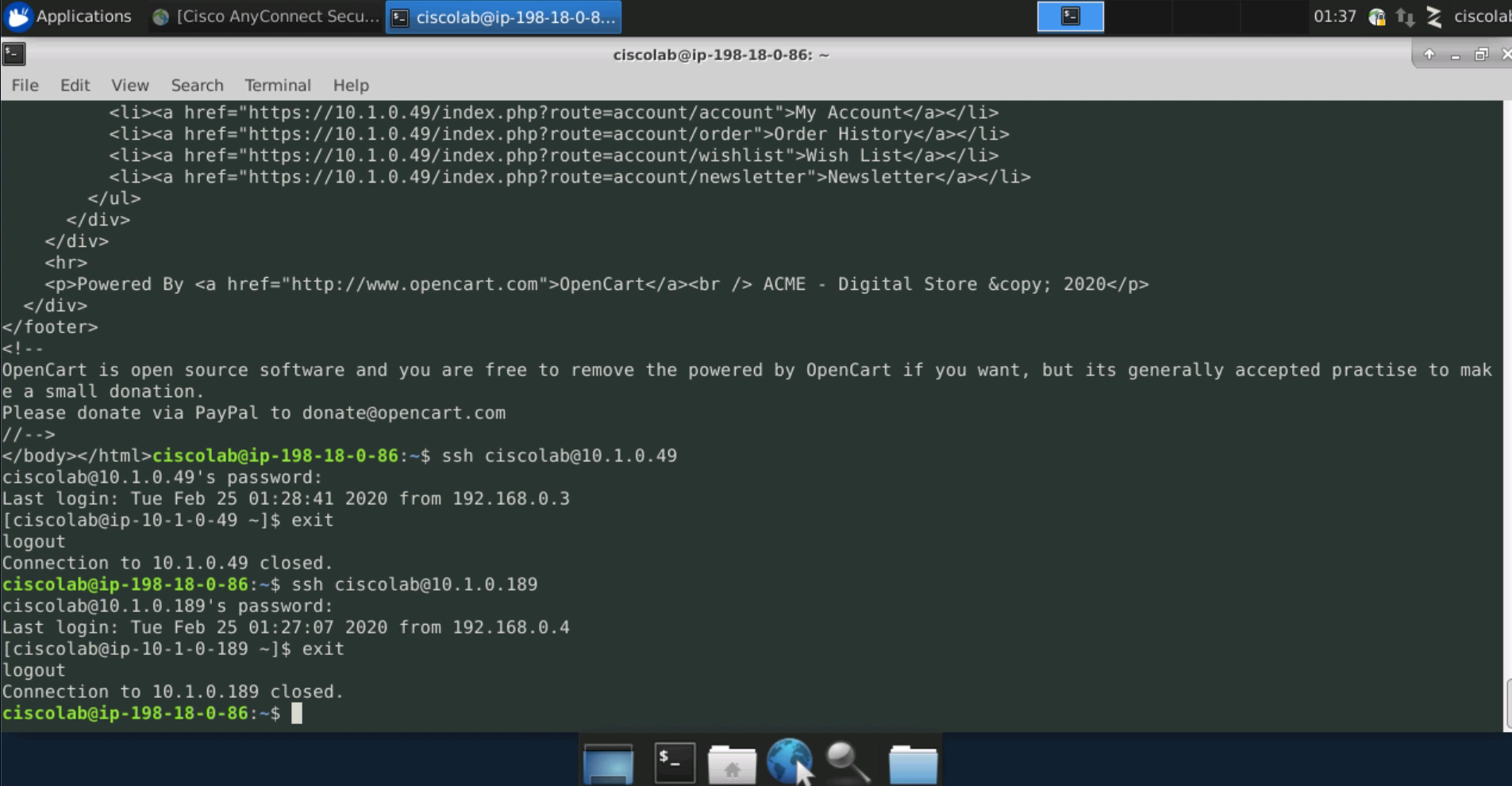
From the SysAdmin desktop, attempt to SSH to the Apache web server and the MySQL server. The connections should both be successful.
Return to the Employee desktop and attempt SSH connections to both the Apache web server and the MySQL servers. Both of these connections should time out because we have not configured rules to allow Employees to SSH to the servers.
Open a session to the Kali Linux server.
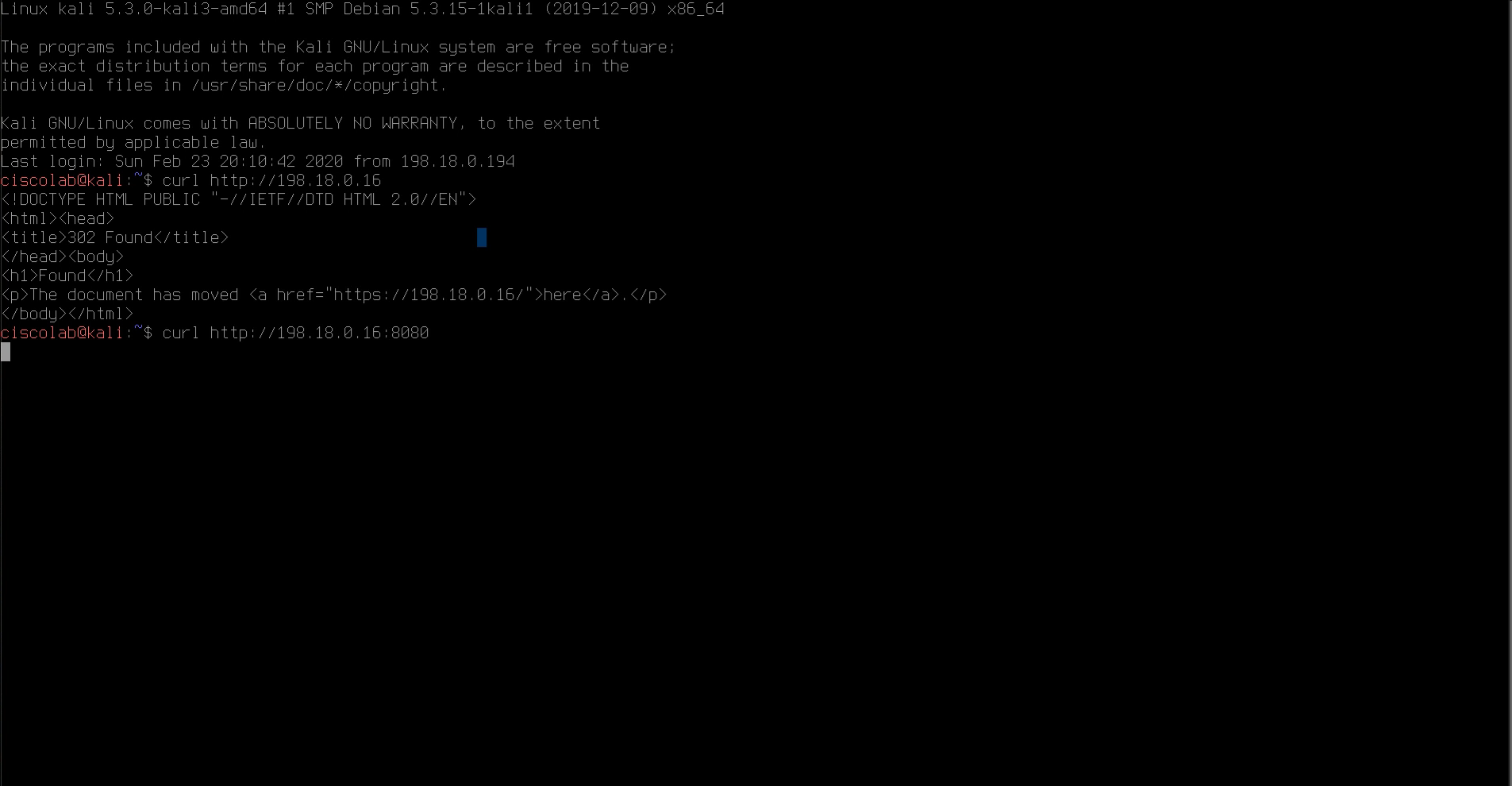
Attempt a HTTP session to the Apache web server using the curl command as shown in the image. Output should be returned for the connection on TCP port 80. Now attempt a connection on TCP port 8080 using the curl command shown in the image. This connection should time out, as we have blocked external access to the application on TCP port 8080.
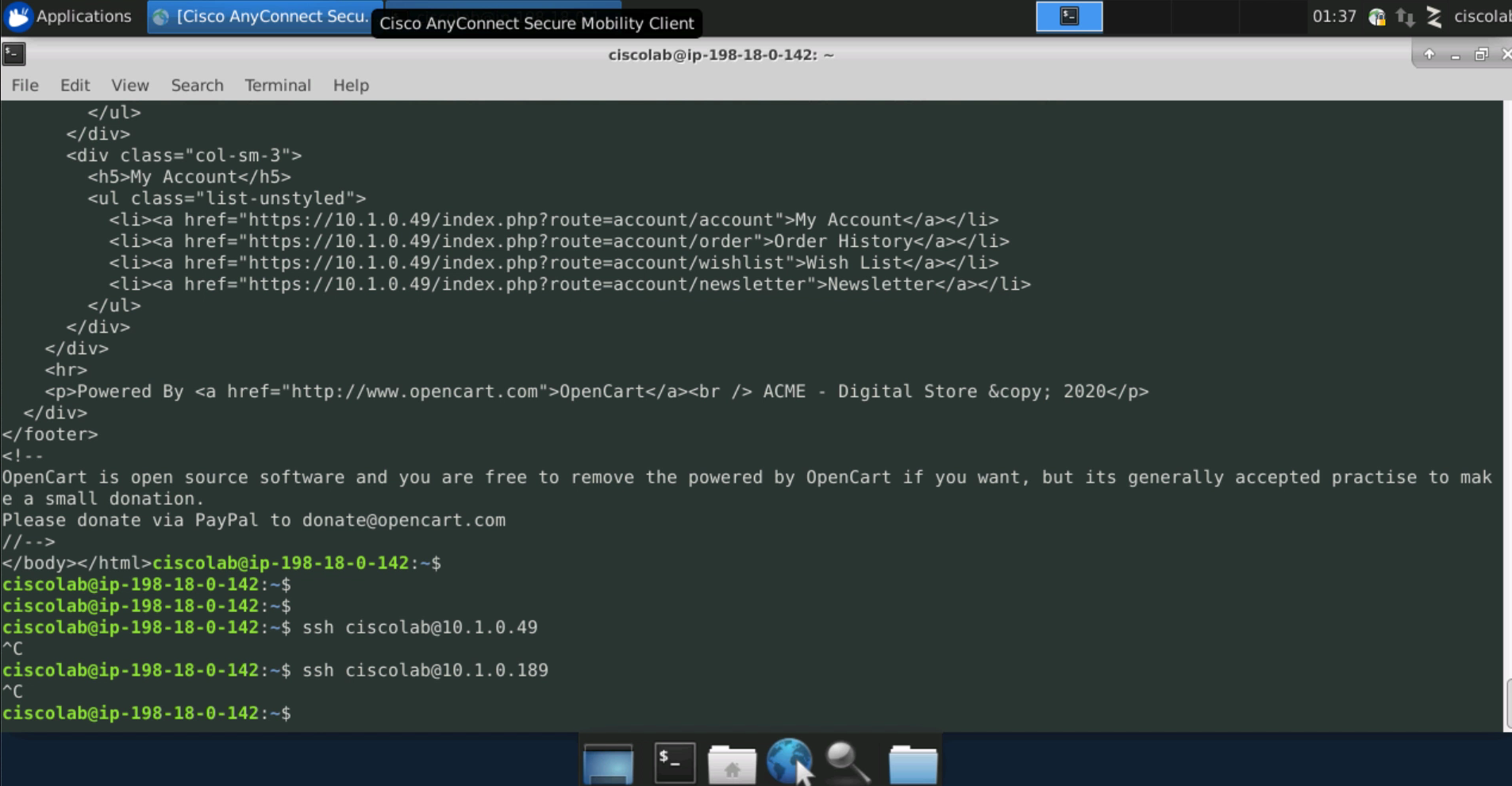
Return to the Employee desktop, and attempt a curl command to the Apache web server on port 8080 as shown in the image. This connection should be successful because we have created a rule to explicitly allow employees to connect to the server on port 8080.
The below image shows the output from the previous curl command.
Open a connection to the IIS web server.
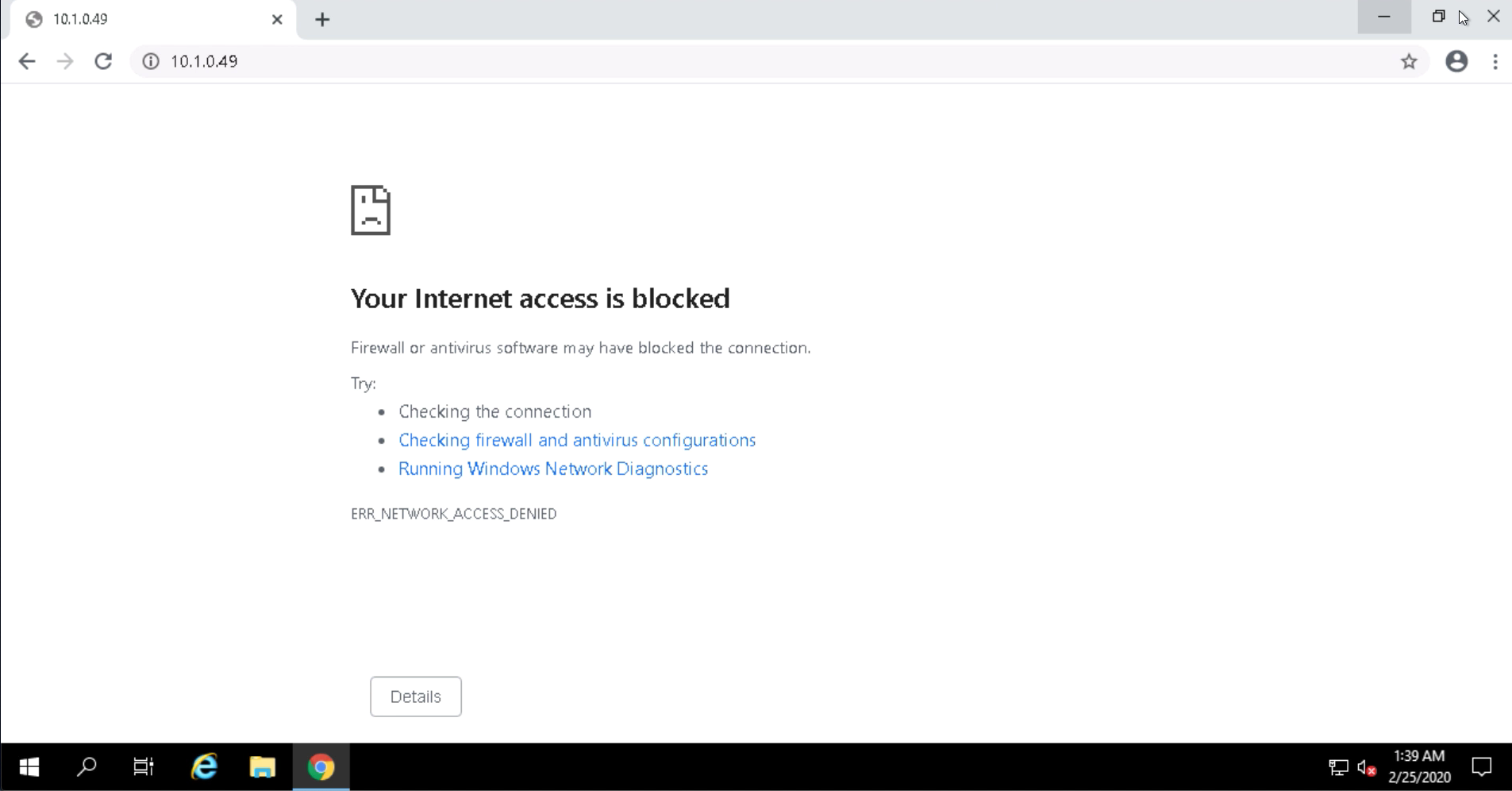
Attempt to connect to the Apache web server in a web browser. The connection should be blocked as we have not created any rules to allow the IIS web server to talk to the Apache web server, nor would we want to allow the communication.
Open a session to the Apache web server.
Attempt a connection from the Apache web server to the IIS web server using the curl command. The connection should time out.
YOU HAVE FINISHED THIS MODULE
| Return to Table of Contents | Go to Top of the Page | Continue to the Next Module |