Cisco Tetration - Hands-On Lab
Module22: Policy Enforcement - Global Services and Common Policies
In this module we will enable Enforcement on the Global Services and Common Policies application workspaces. This will cause rules to be generated on the hosts in Windows Firewall in the case of Windows and iptables on the Linux hosts.
Steps for this Module
Step 001 - Open a session to the MS Active Directory server
Step 002 - Search for and open Windows Firewall
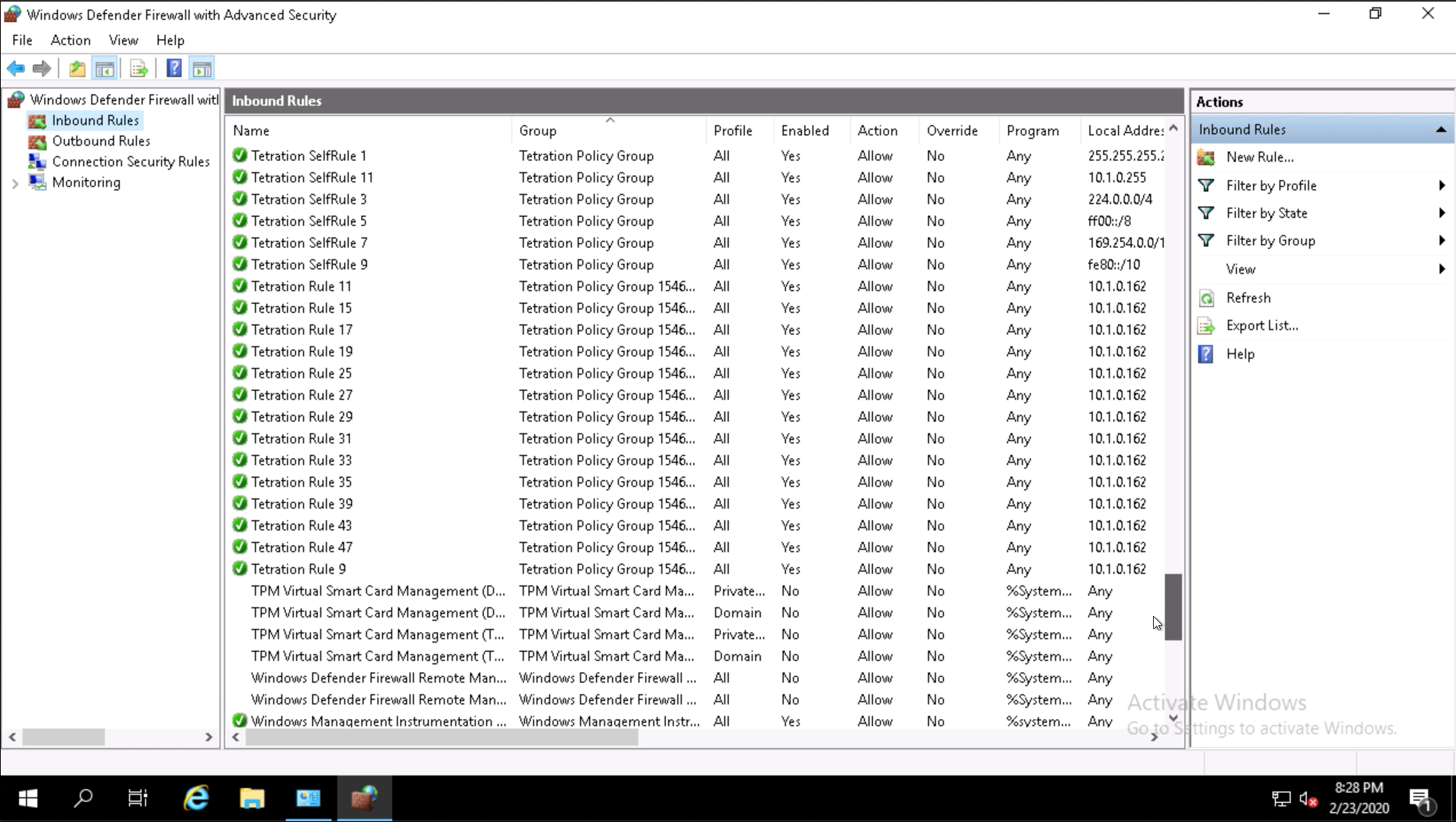
Step 003 - View Inbound Rules
Step 004 - Examine Tetration rules
Step 005 - Navigate to Inventory Search
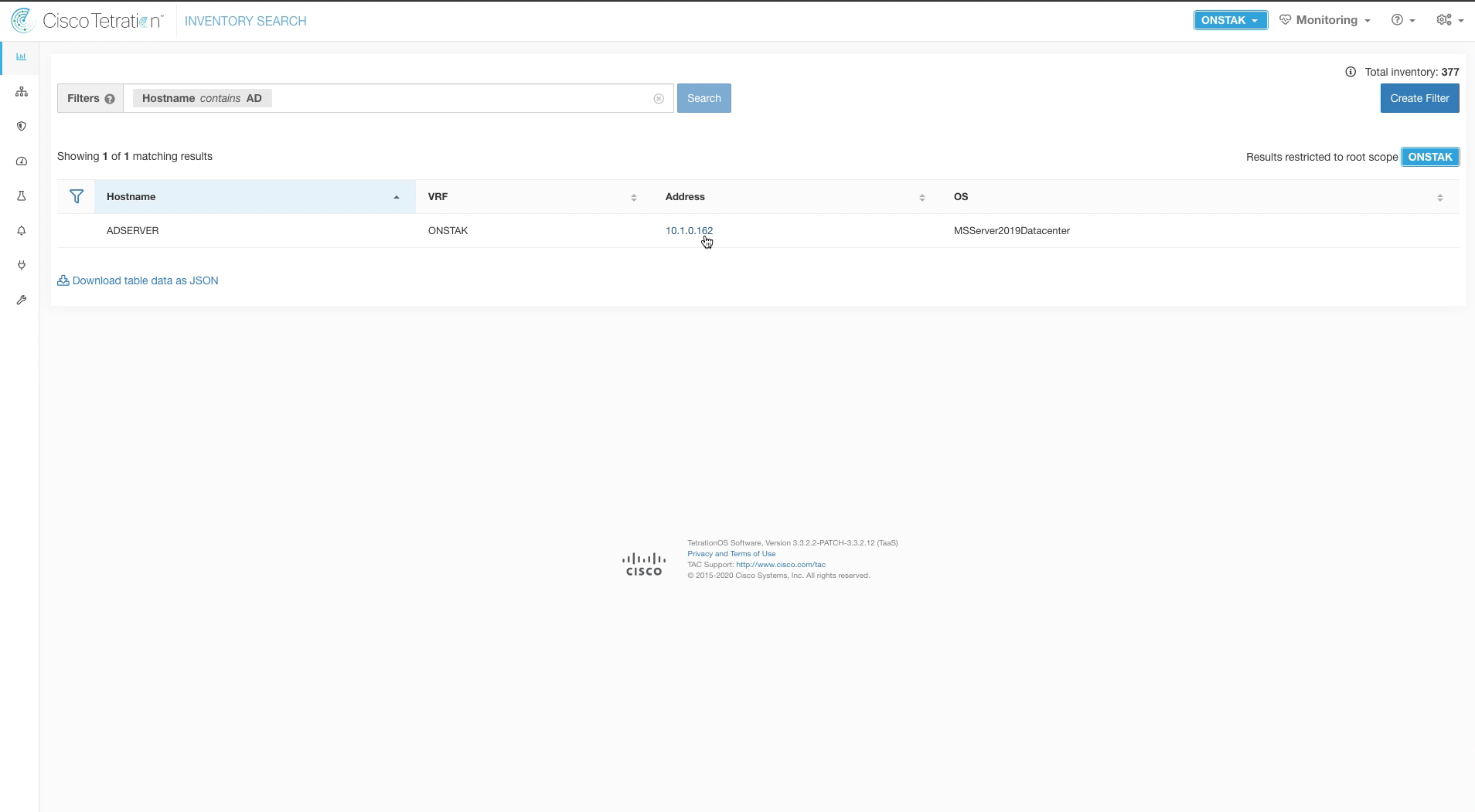
Step 006 - Search for AD server
Step 007 - Navigate to Policies
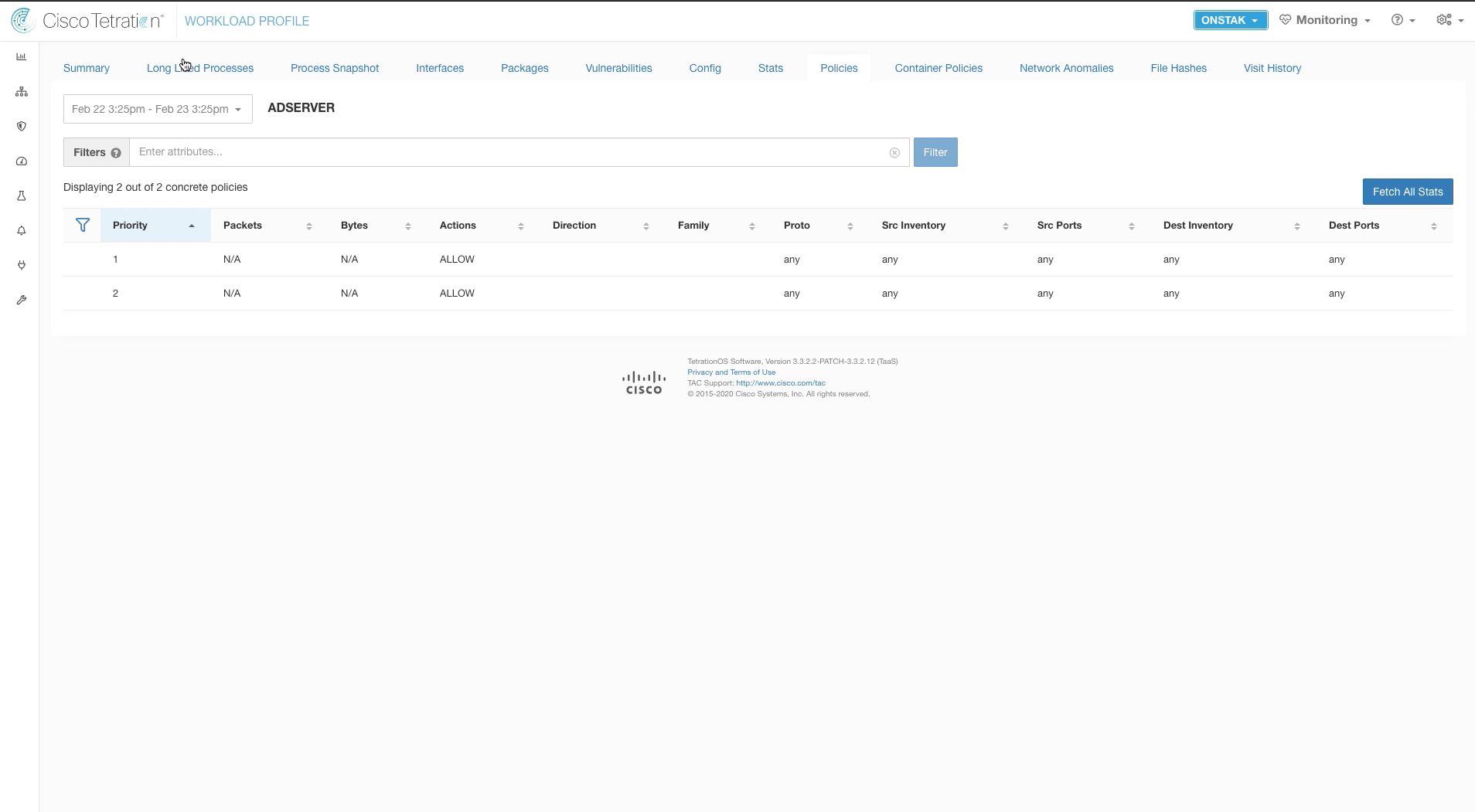
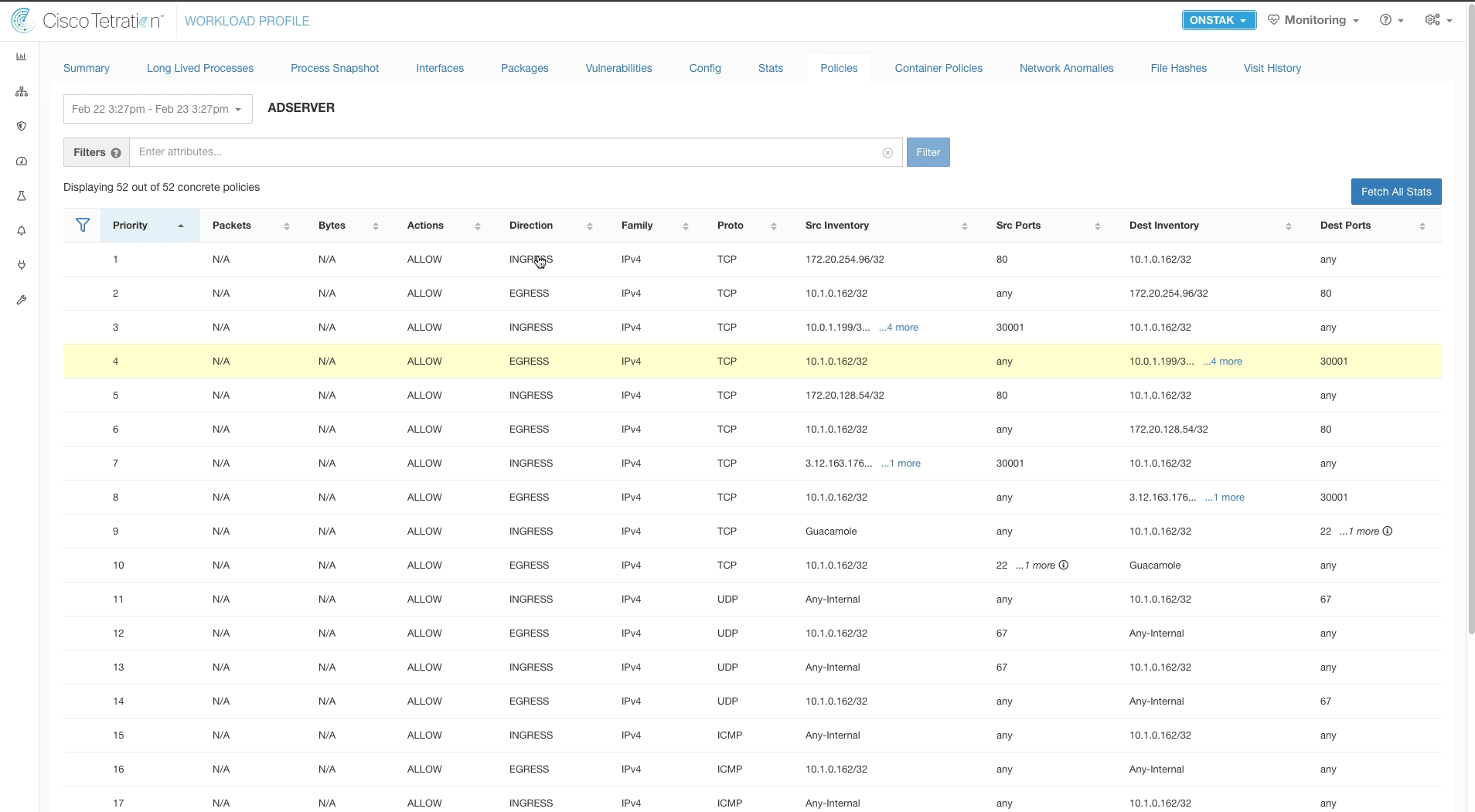
Step 008 - View current Policies
Step 009 - Enable enforcement for Global Services
Step 010 - Choose policy version to enforce
Step 011 - Navigate to the Common Policy app workspace
Step 012 - Enable enforcement on Common Policy
Step 013 - Choose policy version to enforce
Step 014 - Navigate to Inventory Search
Step 015 - Enter workload profile for the AD server
Step 016 - Navigate to Policies
Step 017 - View the Policies
Step 018 - View new rules created in Windows Firewall
Open a session to the Active Directory server.
Click on the Search icon in the toolbar and search for “Firewall”. Open the Windows Defender Firewall control panel.
Click on Inbound Rules.
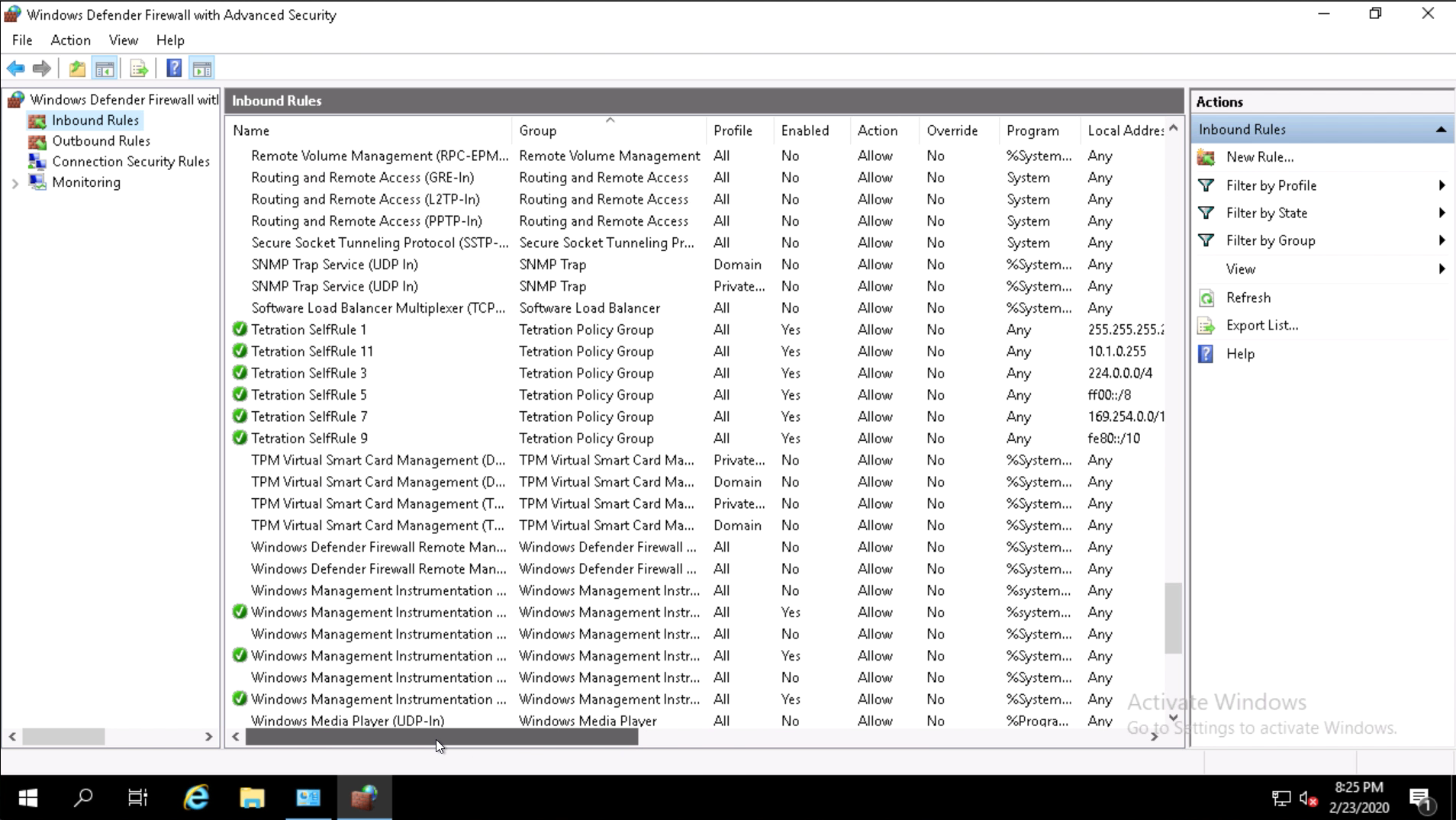
Scroll down to locate the Tetration rules. There will be a few rules that are created by default by Tetration.
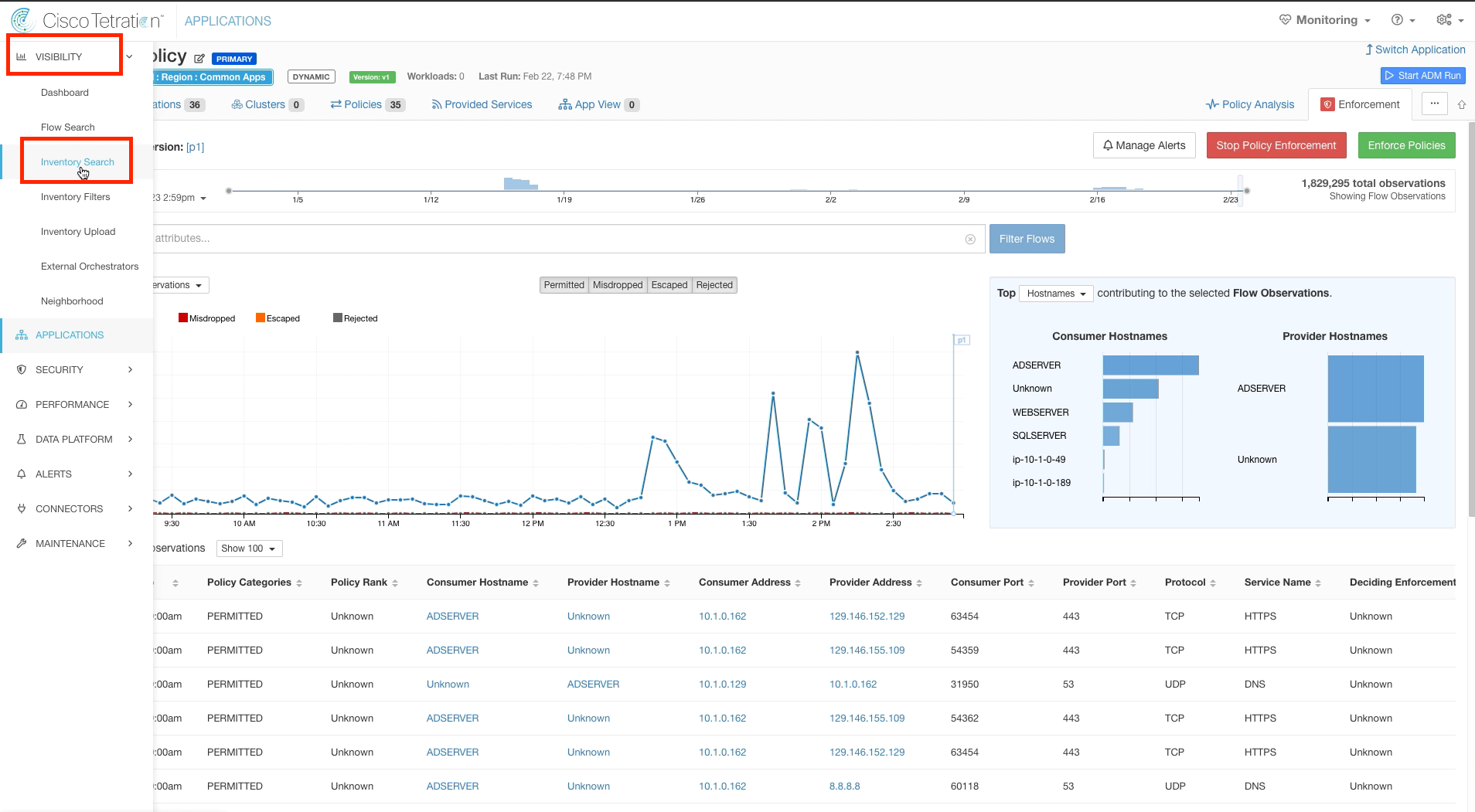
Navigate to Inventory Search.
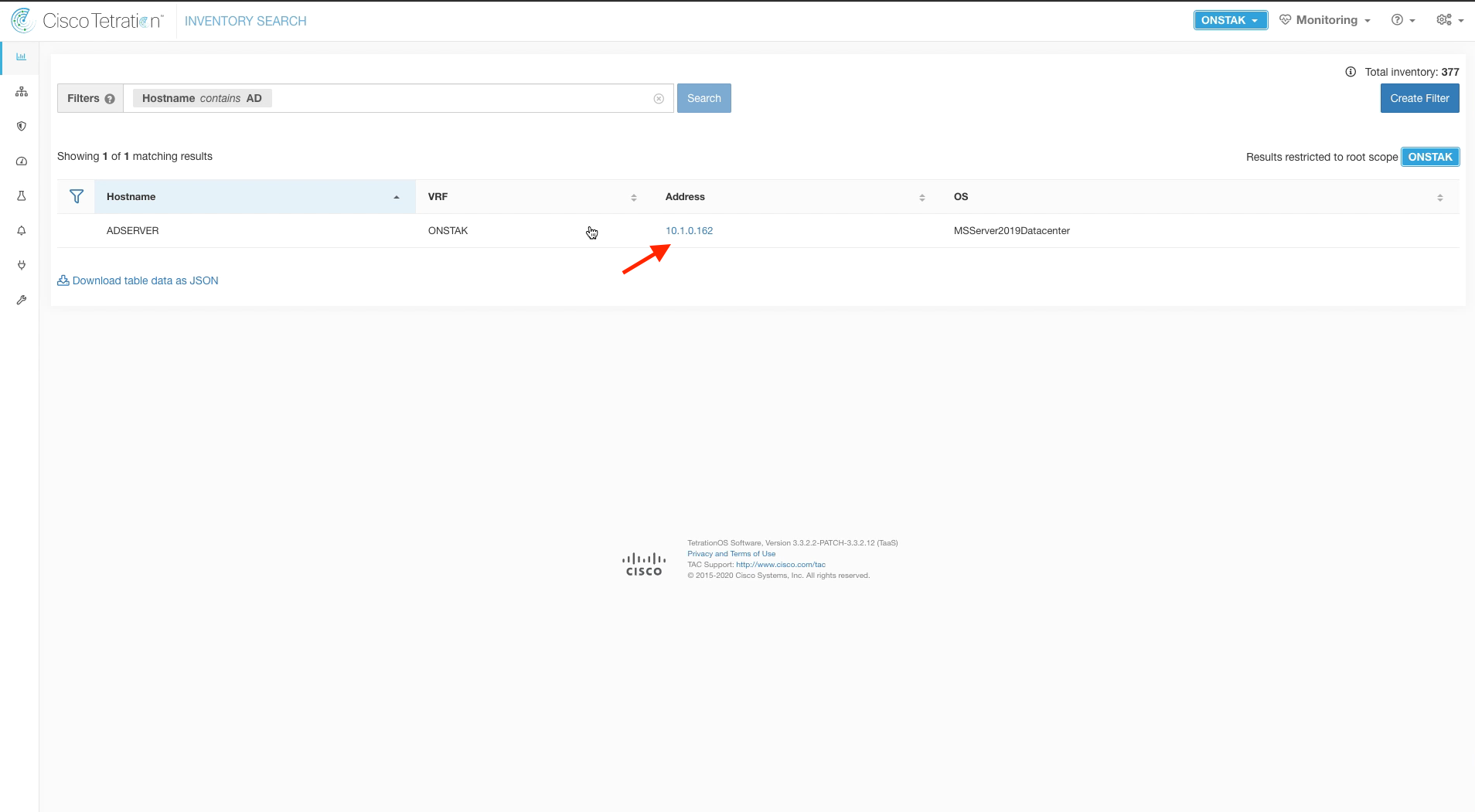
Enter the Filter Hostname contains AD and click on the AD server IP address.
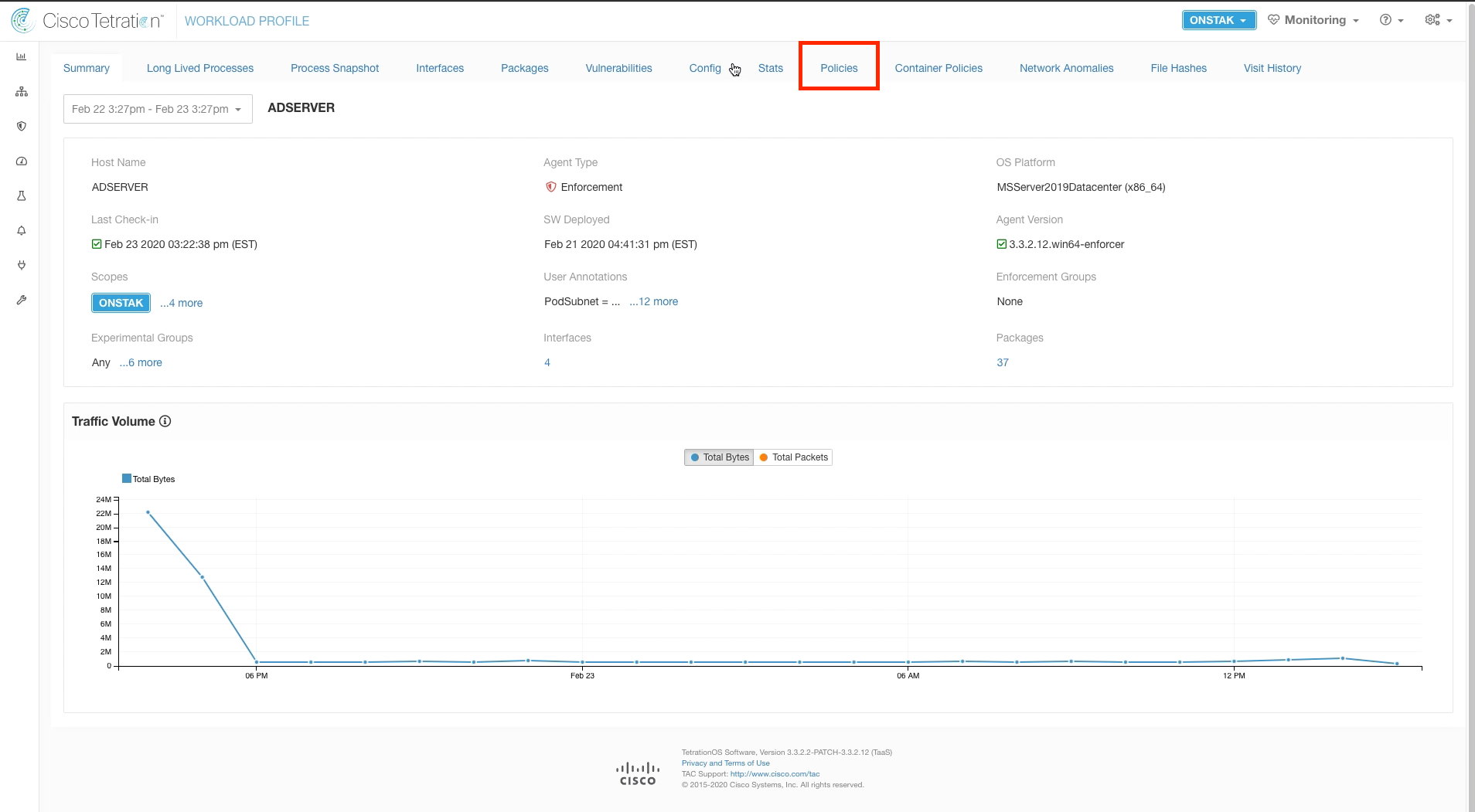
Click on Policies.
Notice there are only two ALLOW rules here with any to allow communication on all ports and protocols.
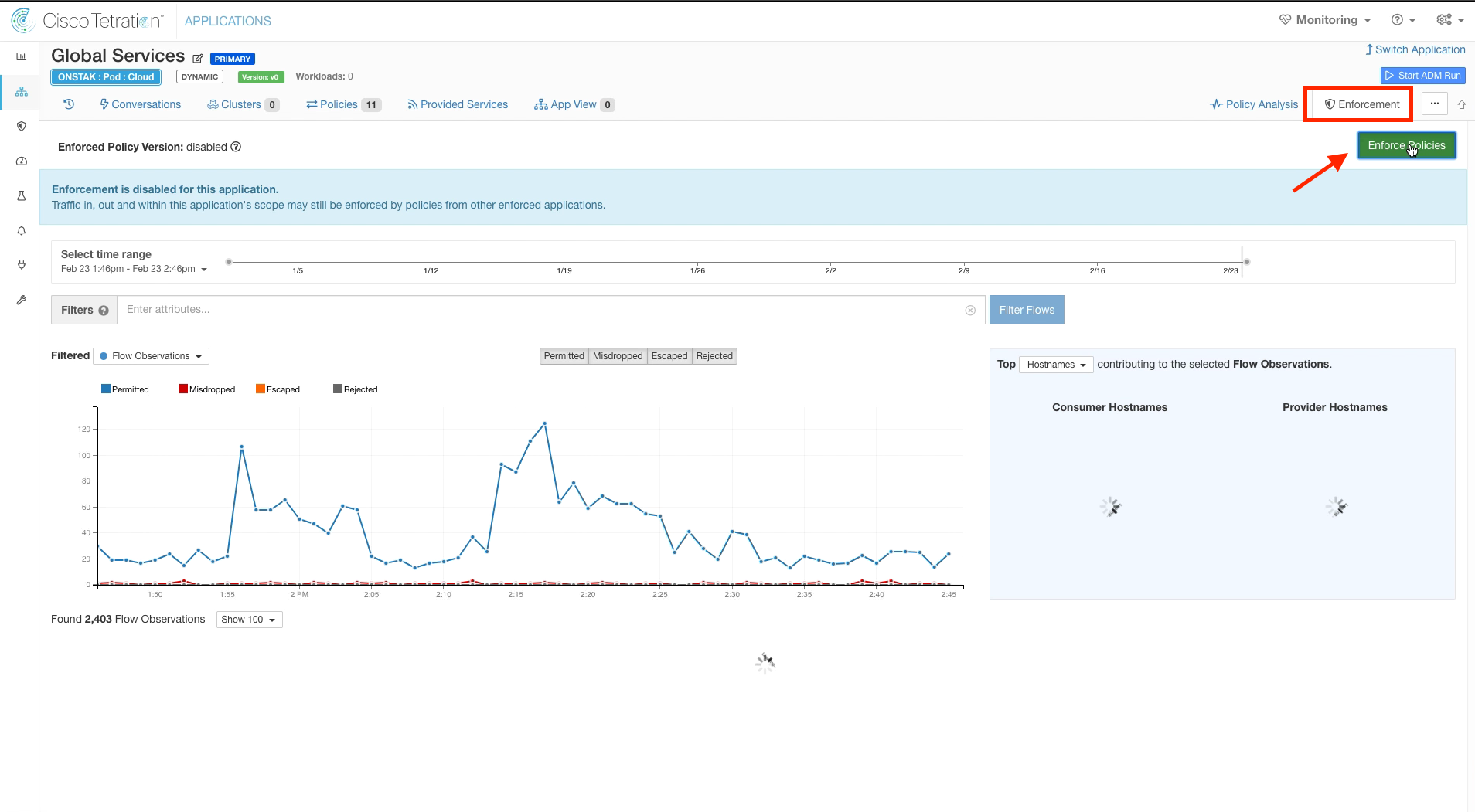
Navigate to the Global Services app workspace and click on the Enforcement tab. Click on Enforce Policies.
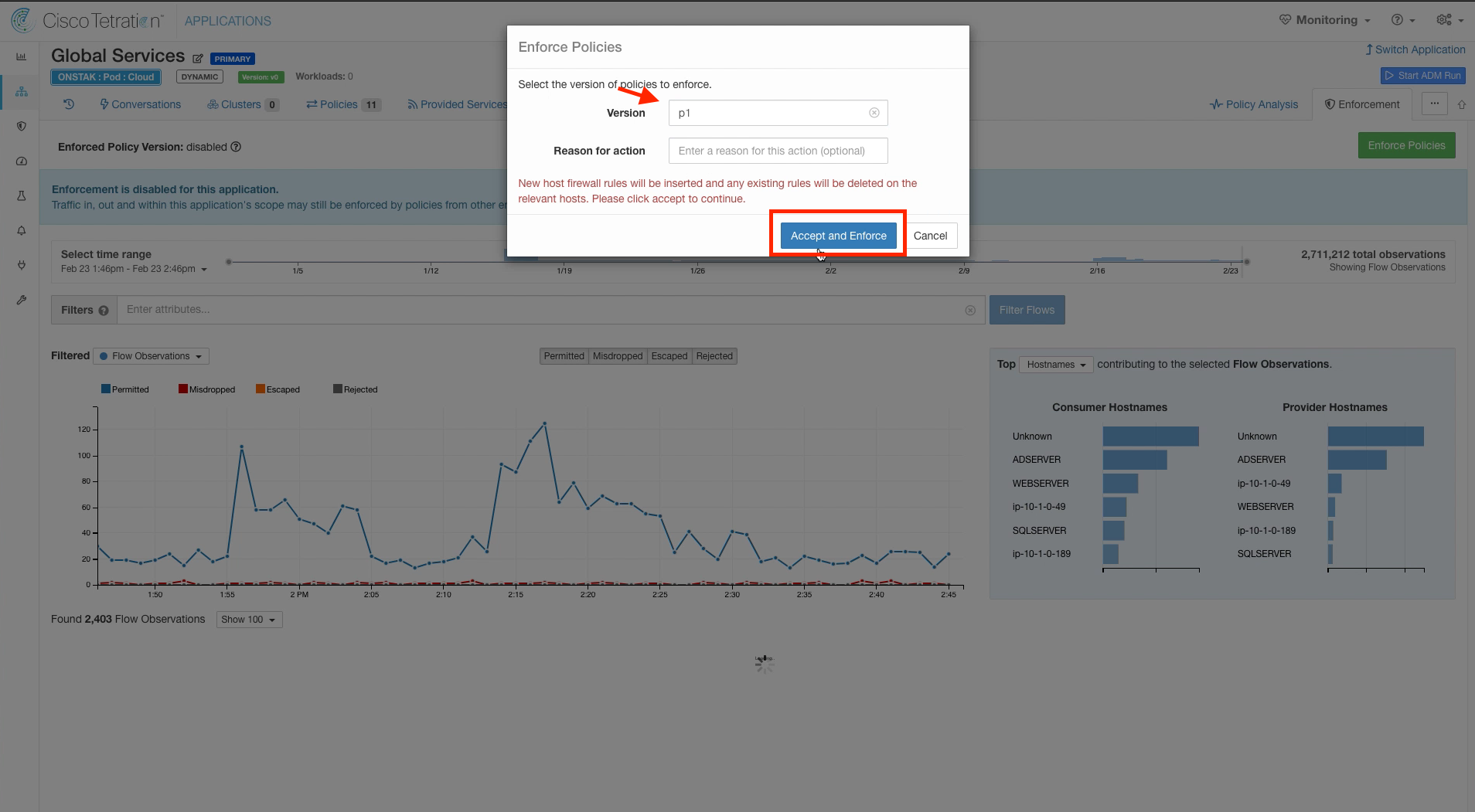
Choose the version of policy to be enforced. Normally this would be the latest analyzed policy, however this could be used to revert an already enforced policy back to a previous version if needed.
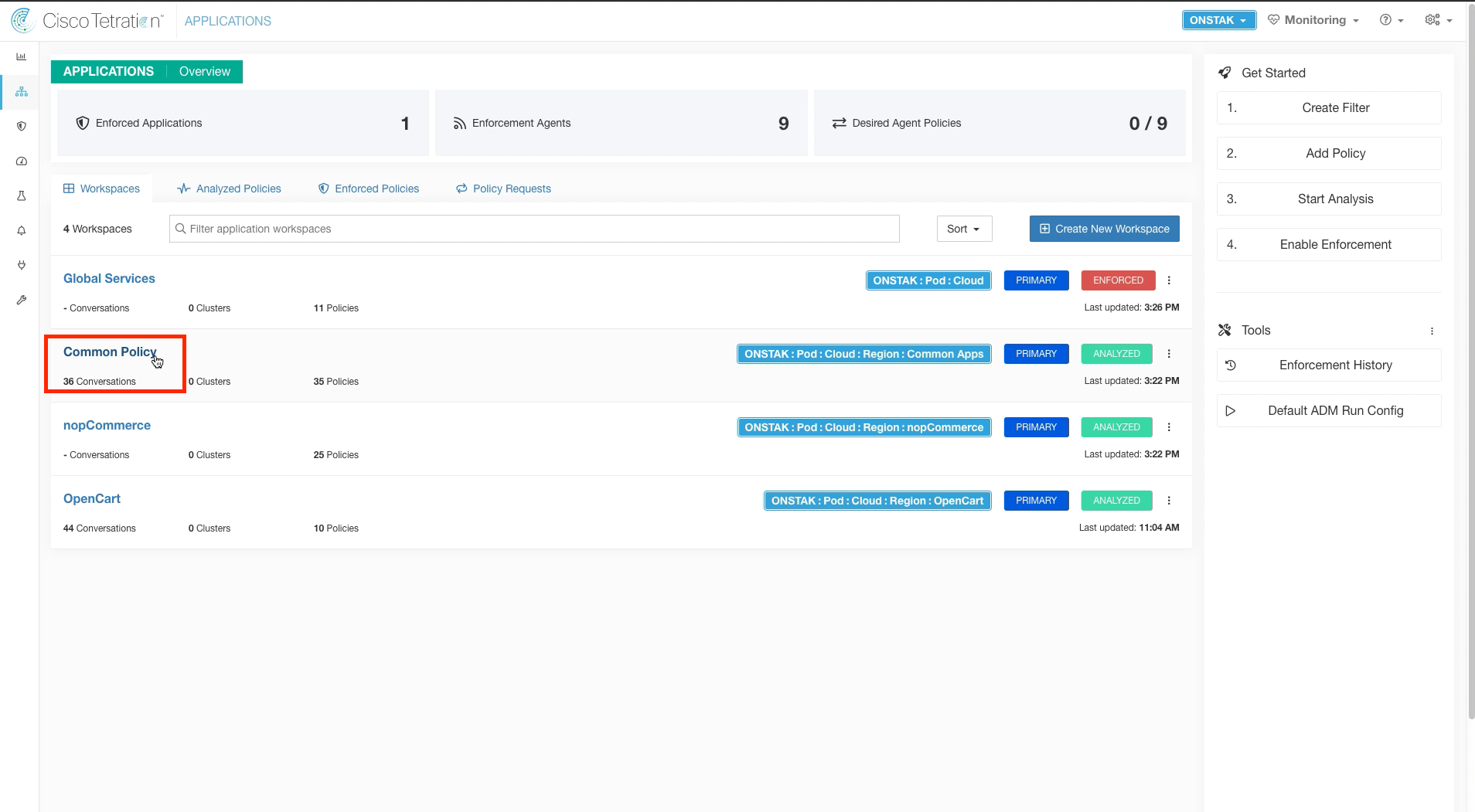
Navigate to the Common Policy application workspace.
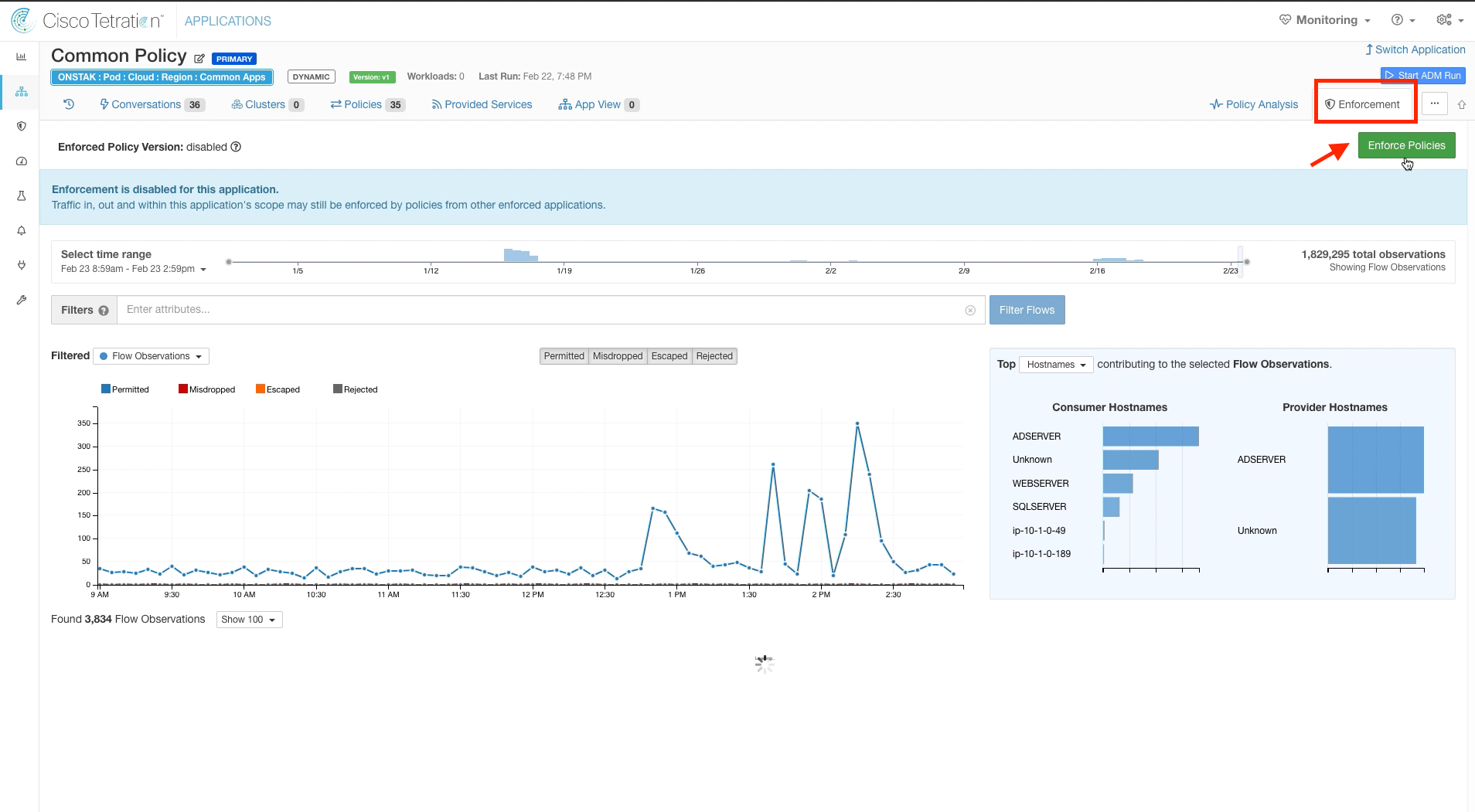
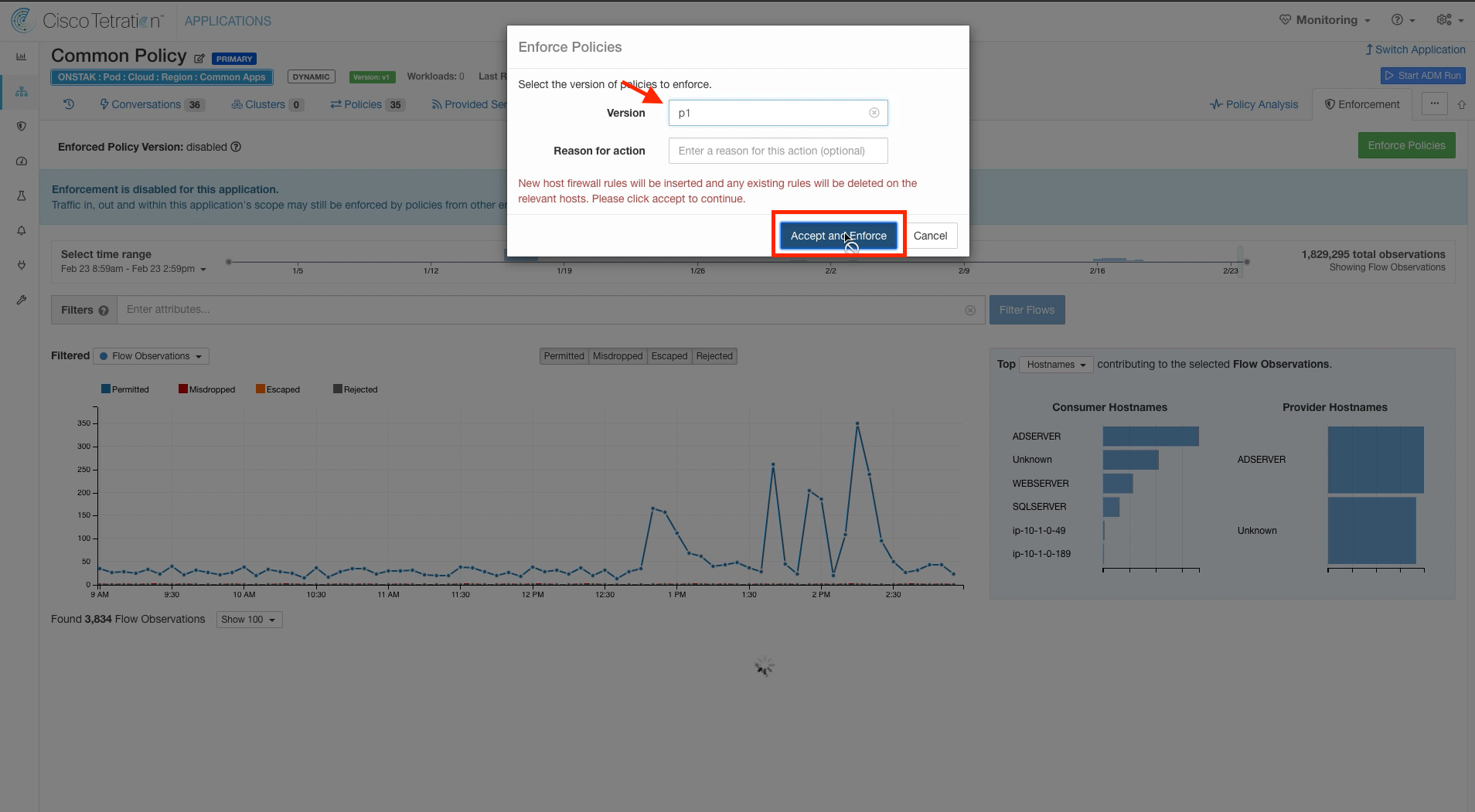
Click on the Enforcement tab and click Enforce Policies.
Select the latest version of policy and click Accept and Enforce.
Navigate to Inventory Search.
Enter the Filter Hostname contains AD, click Search and then click on the AD server IP address.
On the workload profile screen click on Policies.
There should now be many more rules listed here. It may take a minute or so before the new policies are shown. Adjust the time range and refresh the screen as necessary until the new policies show up. These are a representation of the firewall rules that were created in Windows Firewall.
Go back to the session to the AD server, and examine the Inbound Rules in Windows Firewall. There should be many more rules created by Tetration.
YOU HAVE COMPLETED THIS MODULE
| Return to Table of Contents | Go to Top of the Page | Continue to the Next Module |