Cisco Tetration - Hands-On Lab
Module20: Policy Analysis - OpenCart
In this module we will perform Policy Analysis for the OpenCart application and adjust policy as necessary based on the results. We will also run an Experiment which analyzes the current policy against historical flows that occurred during a specified time range. This can be useful to see what the policy results would have been over a period of weeks or even months based on the traffic observed during that time frame, even before Policy Analysis was enabled for the application.
Steps for this Module
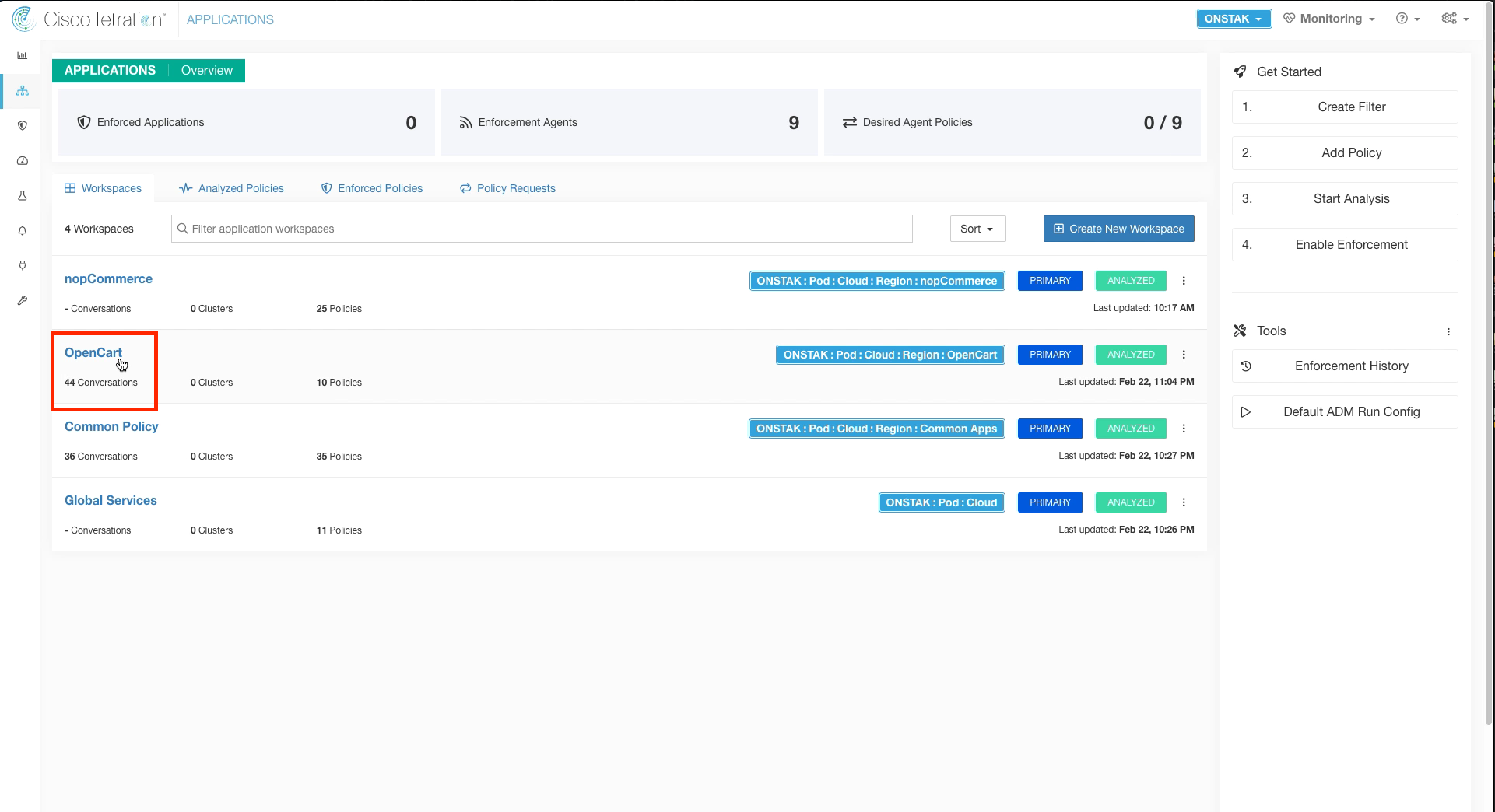
Step 001 - Navigate to the OpenCart application workspace
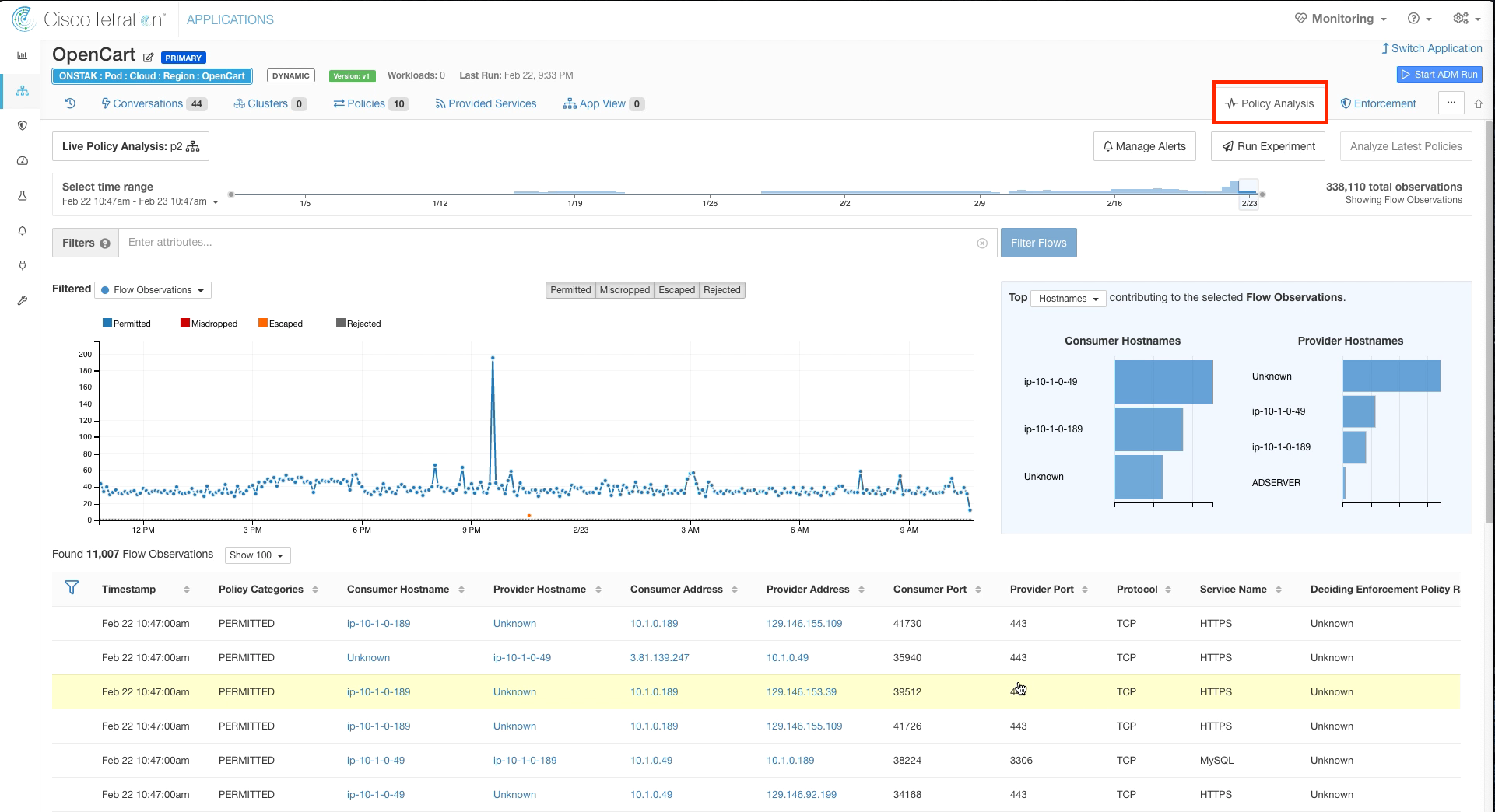
Step 002 - Click on Policy Analysis
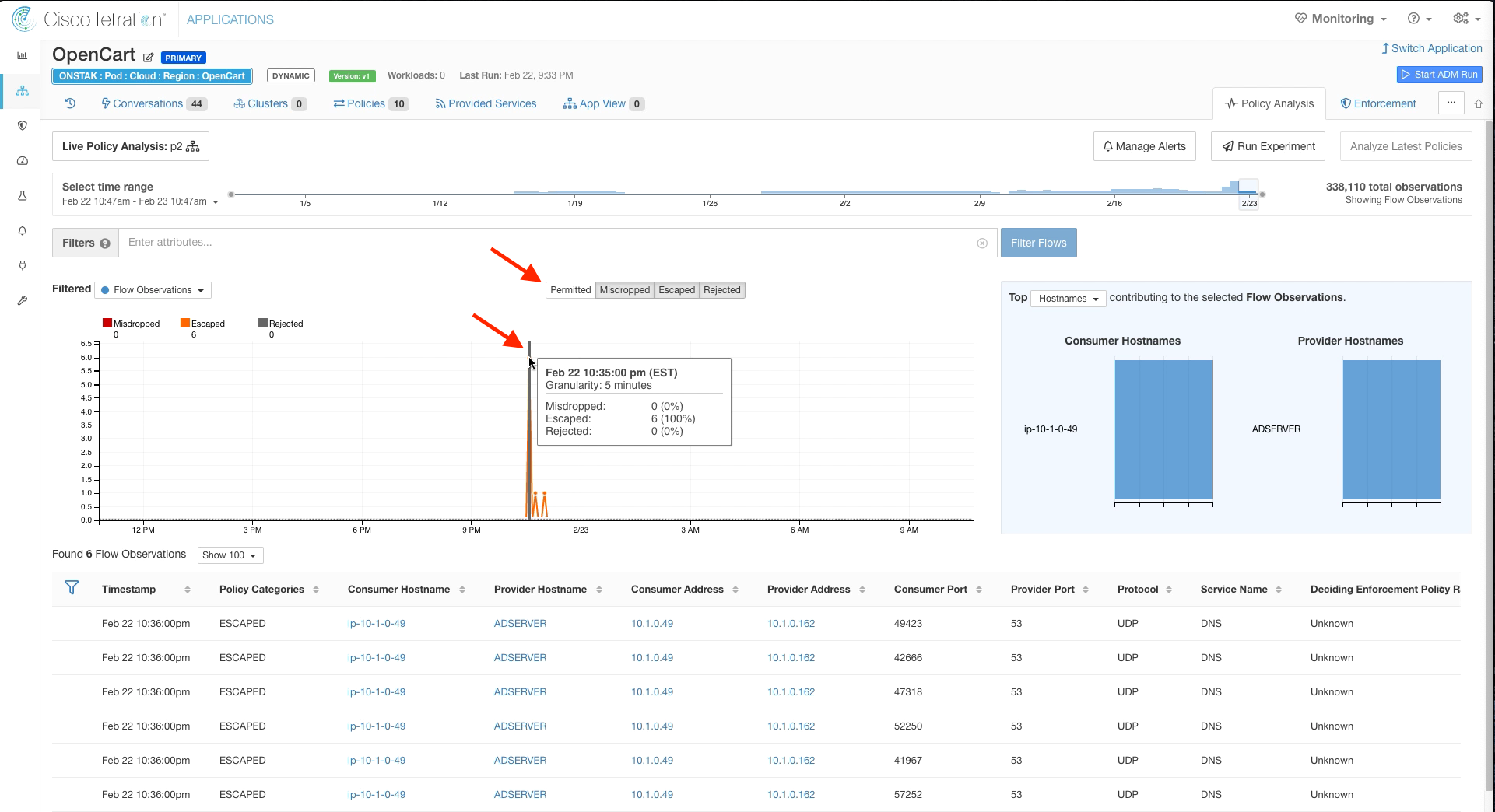
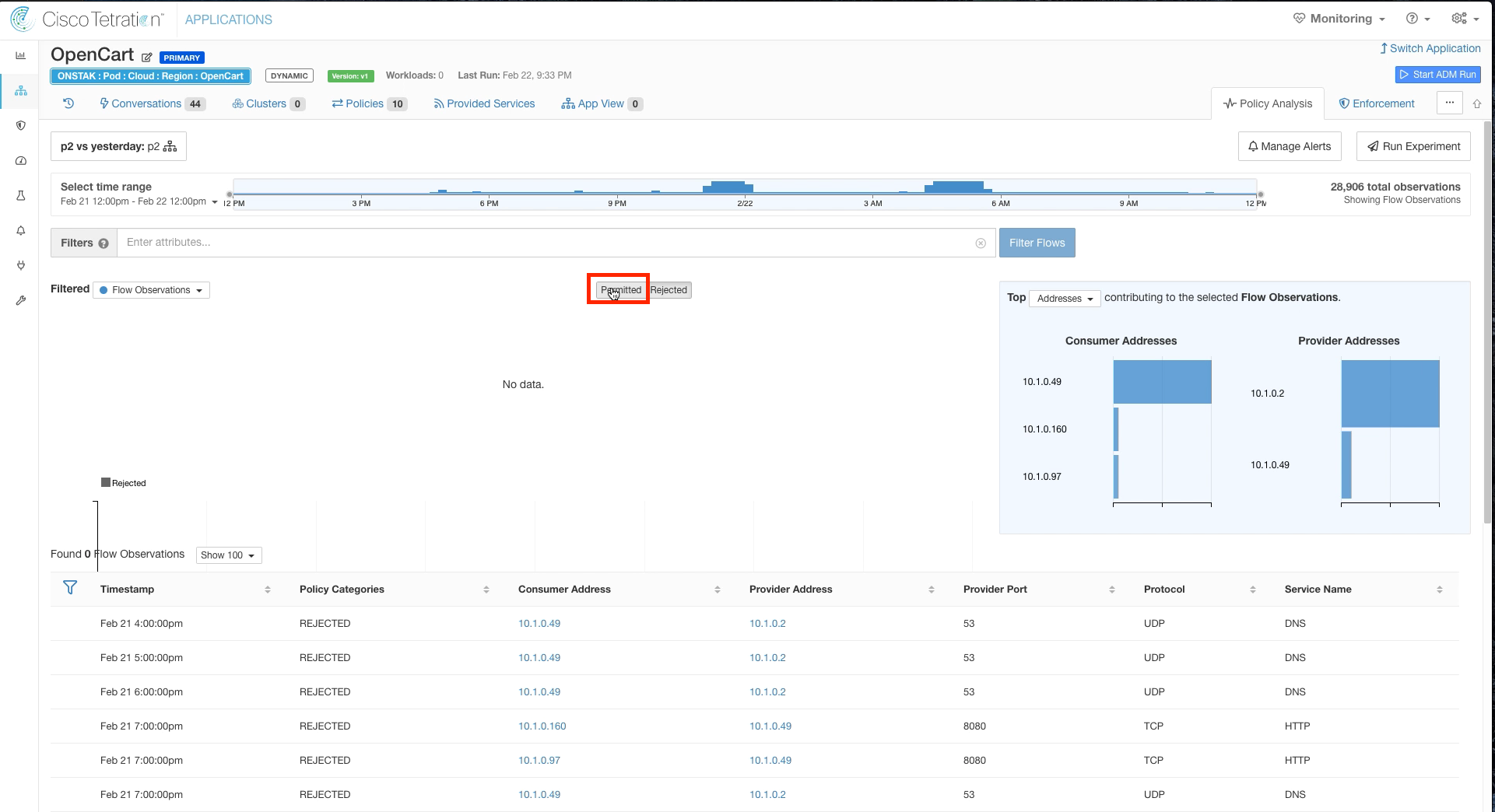
Step 003 - Filter out Permitted flows
Step 004 - Click on the Escaped flow
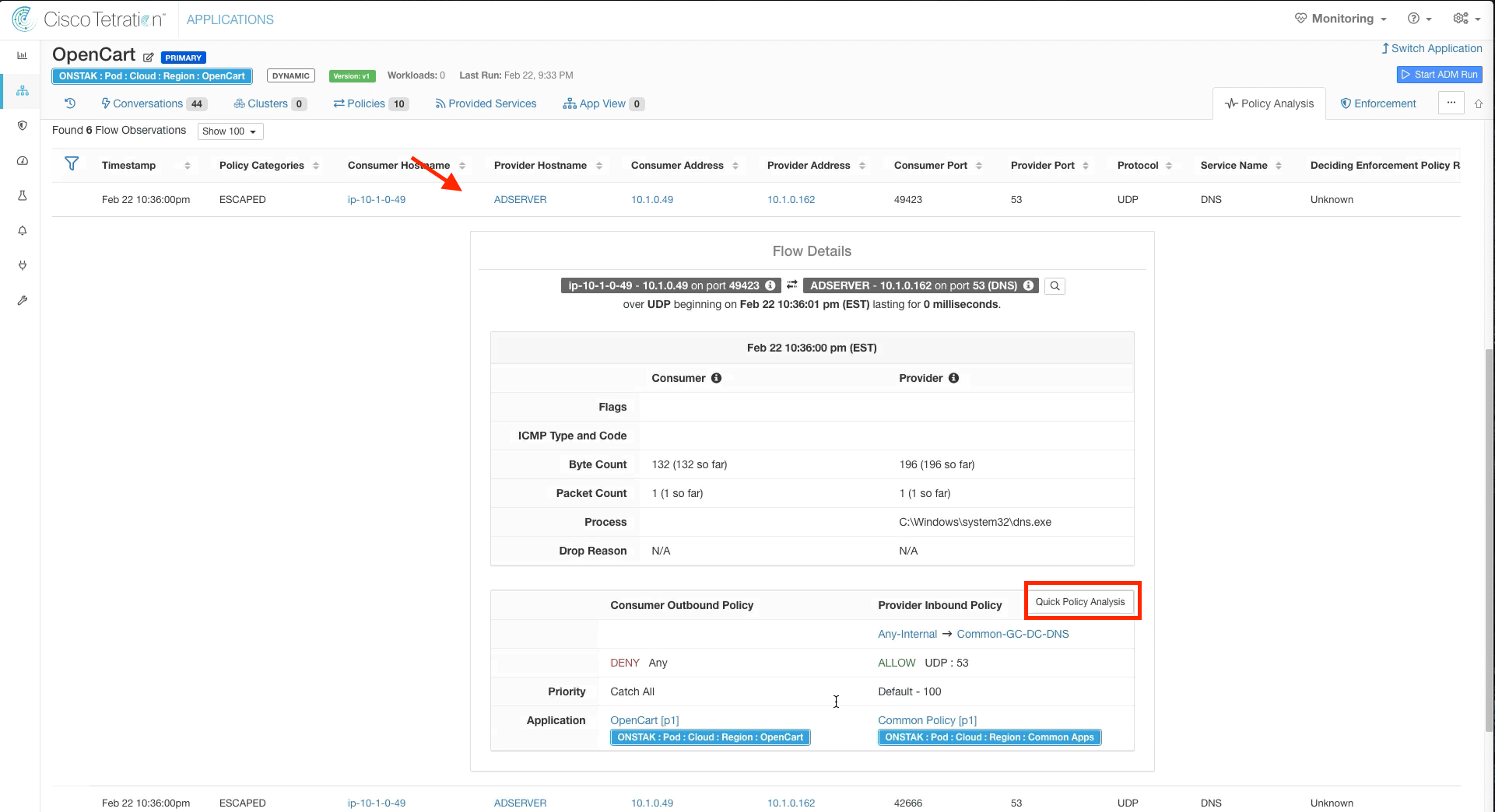
Step 005 - Perform Quick Policy Analysis
Step 006 - View application activity log
Step 007 - Change time range to 1hr
Step 008 - Re-enable viewing of Permitted flows
Step 009 - Click on Run Experiment
Step 010 - Select Start/End Date for Experiment
Step 011 - View progress of experiment
Step 012 - View experiment results
Step 013 - Filter out permitted flows
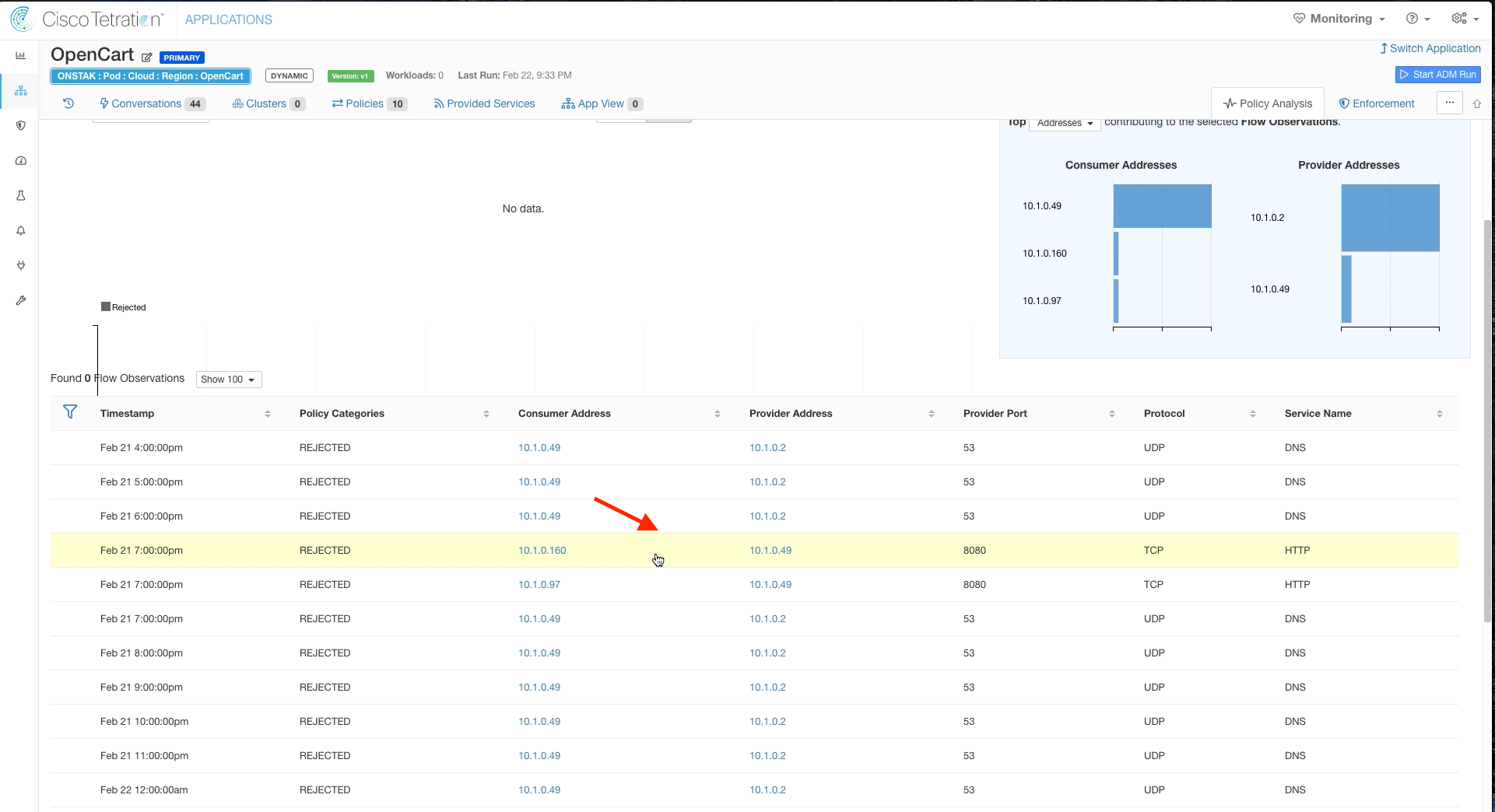
Step 014 - Click on a Rejected flow to TCP port 8080
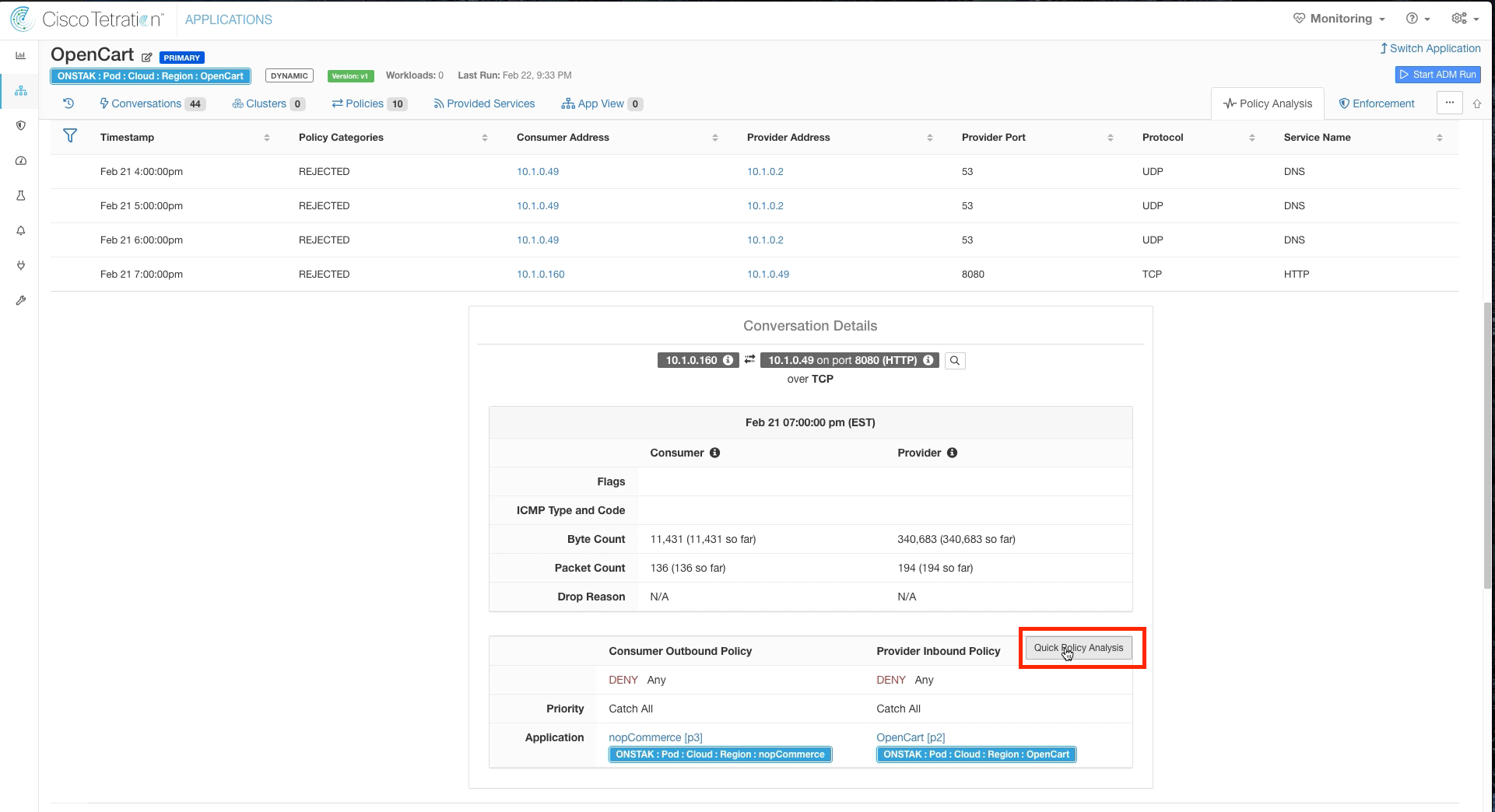
Step 015 - Run Quick Policy Analysis
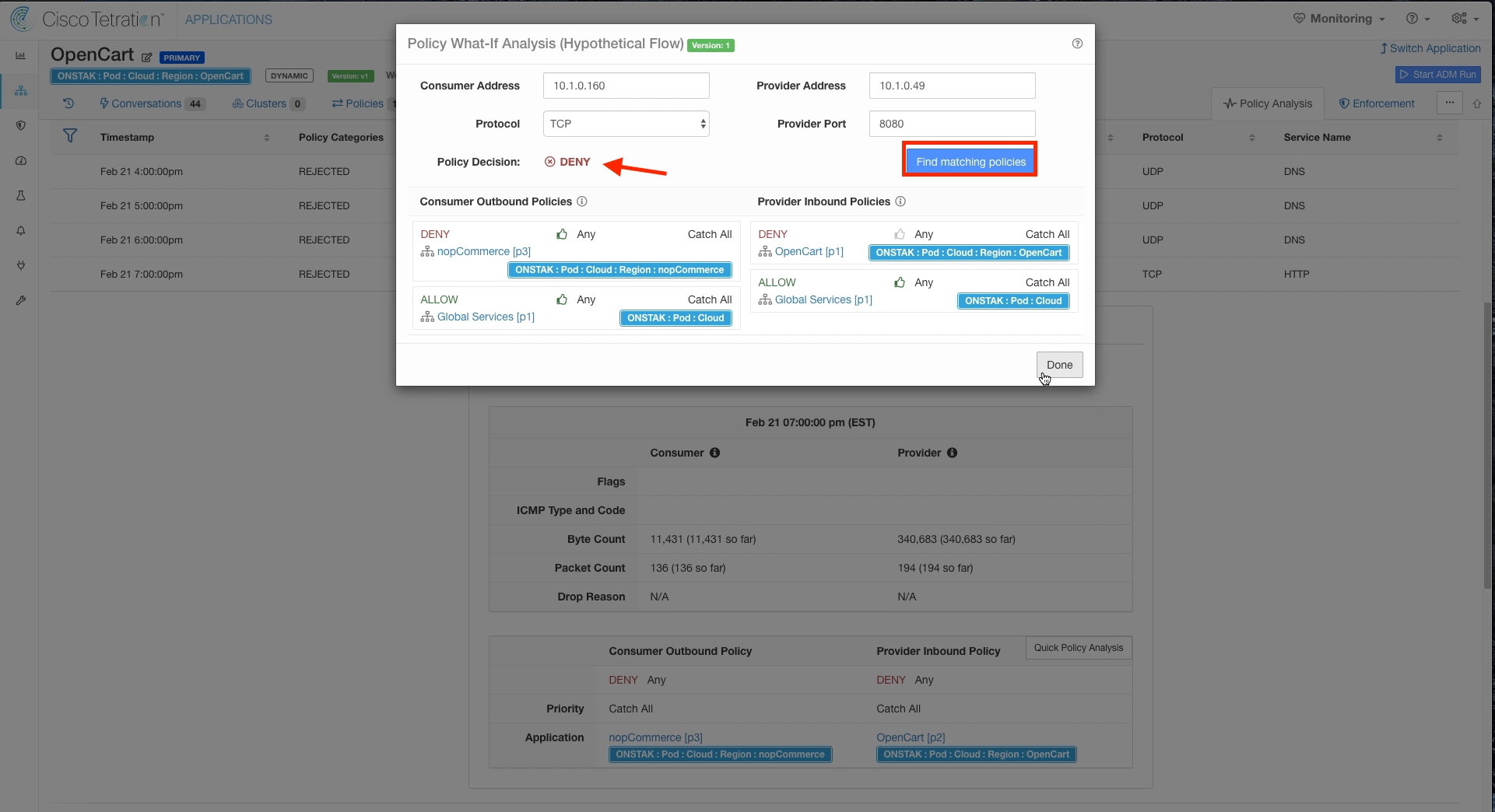
Step 016 - View Quick Policy Analysis results
Navigate to the OpenCart application workspace.
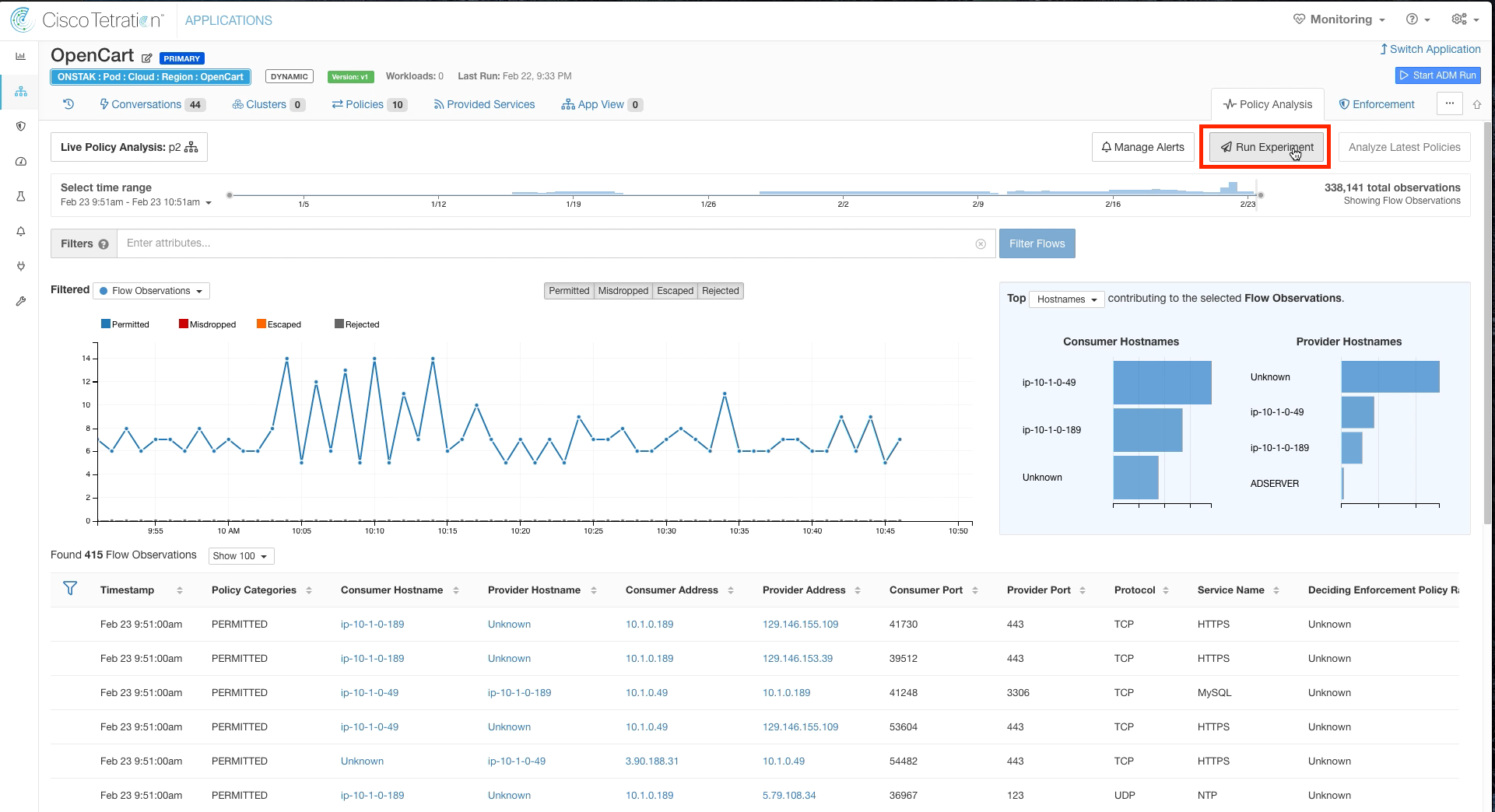
Click on Policy Analysis.
Filter out Permitted flows, and click on the point in the graph where there are Escaped flows (denoted in orange).
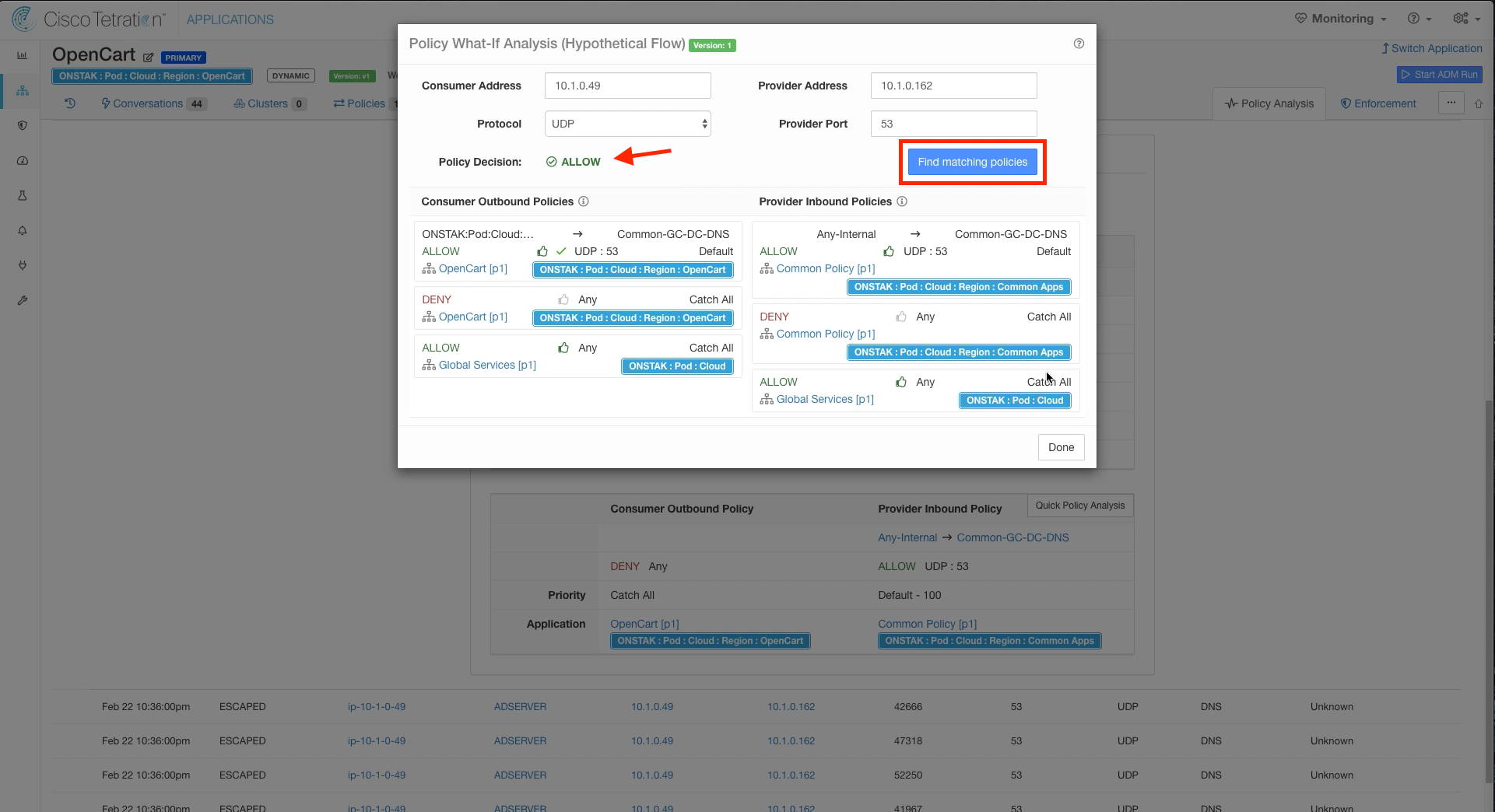
Click on one of the escaped flows, and select Quick Policy Analysis.
Click on Find matching policies. Note that the Policy Decision is ALLOW. Why is the flow indicating escaped but the flow is ALLOW in our policy?
Hint: We haven’t changed the time range! We are looking at a point in the graph prior to our policy change we made earlier in the OpenCart application workspace to allow the OpenCart scope to talk to Common-GC-DC-DNS on UDP port 53.
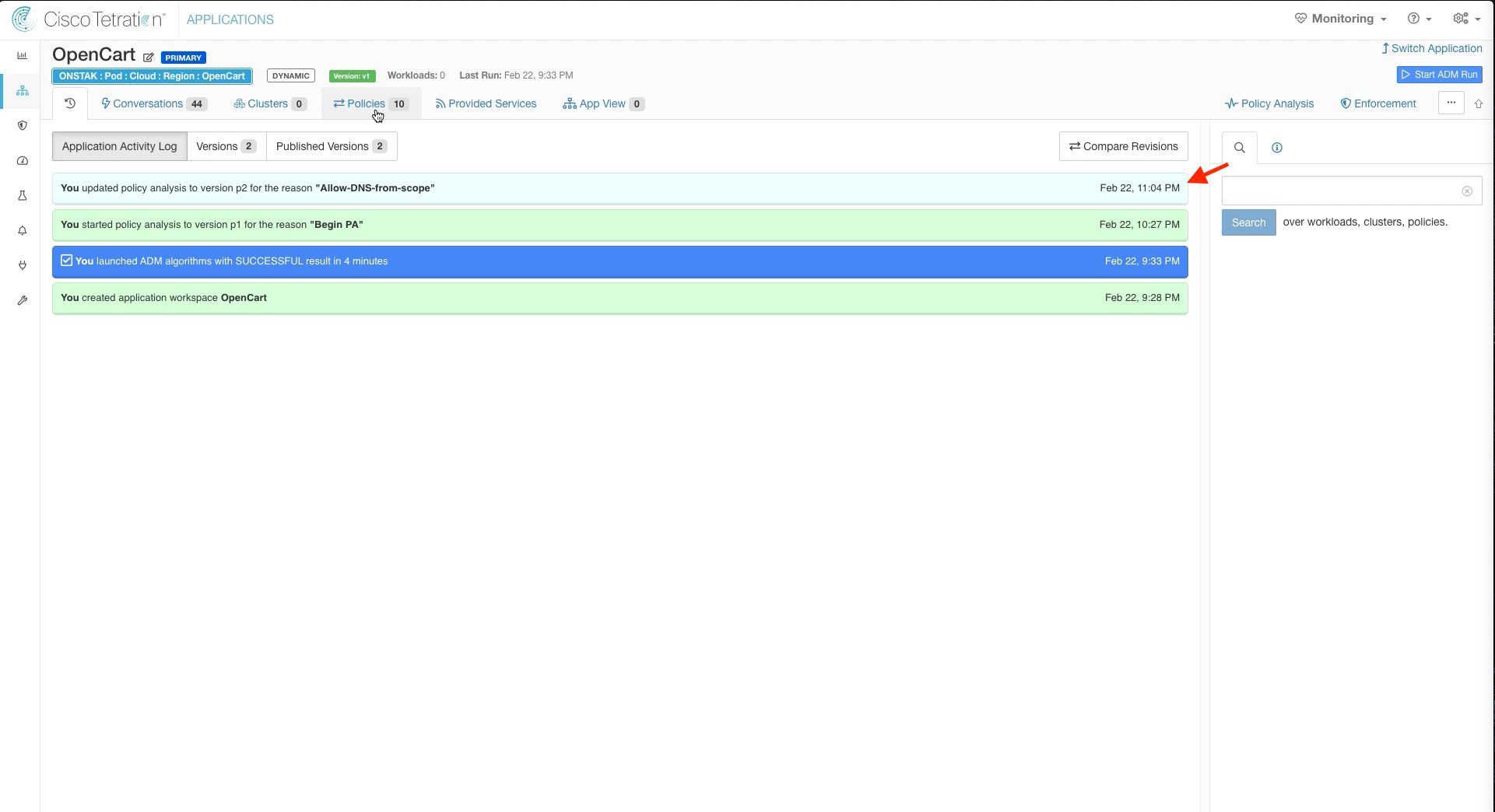
Click on the clock icon and note the last time policy was changed and the reason.
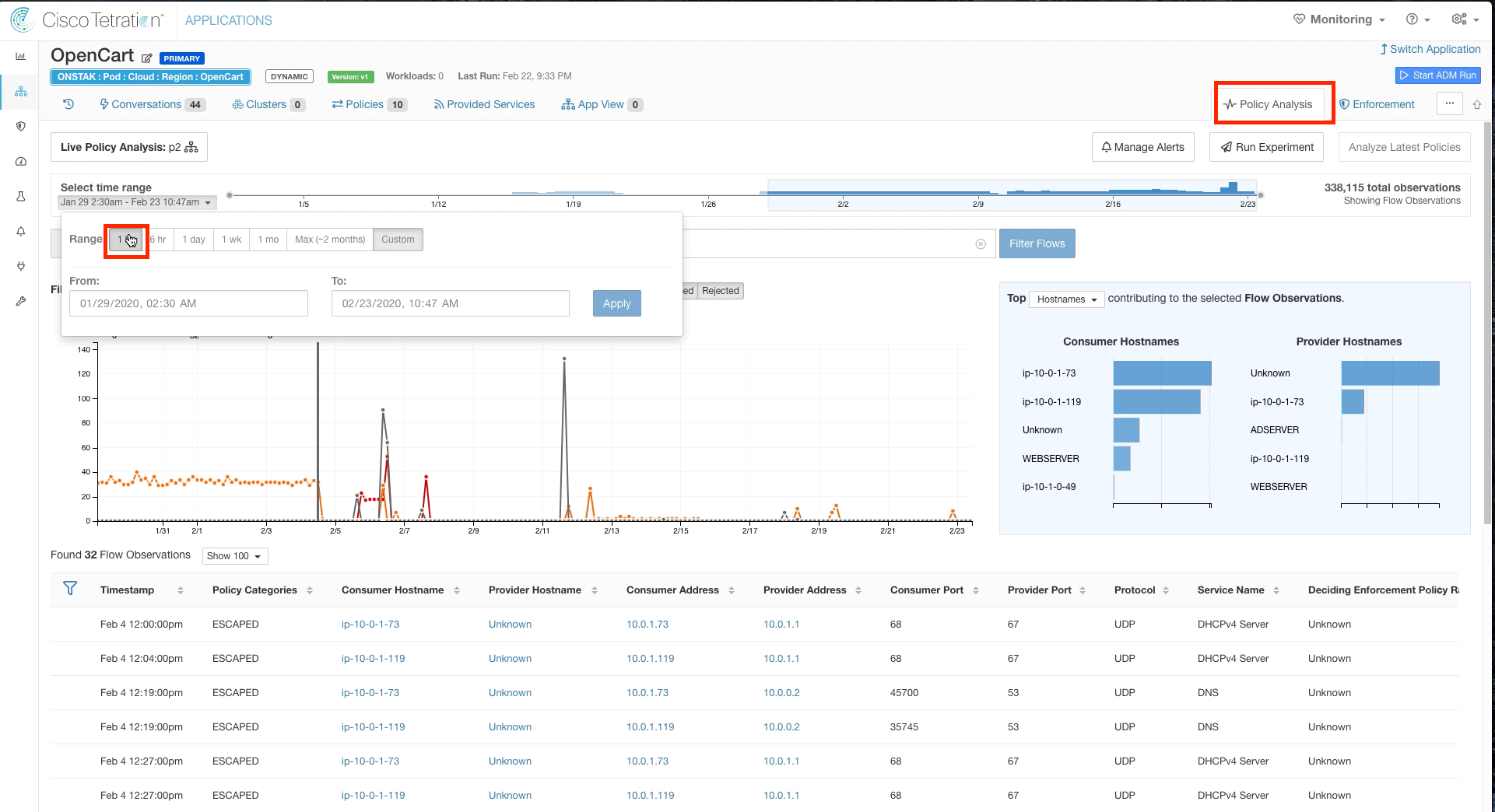
Click on Policy Analysis and change the time range to 1 hour.
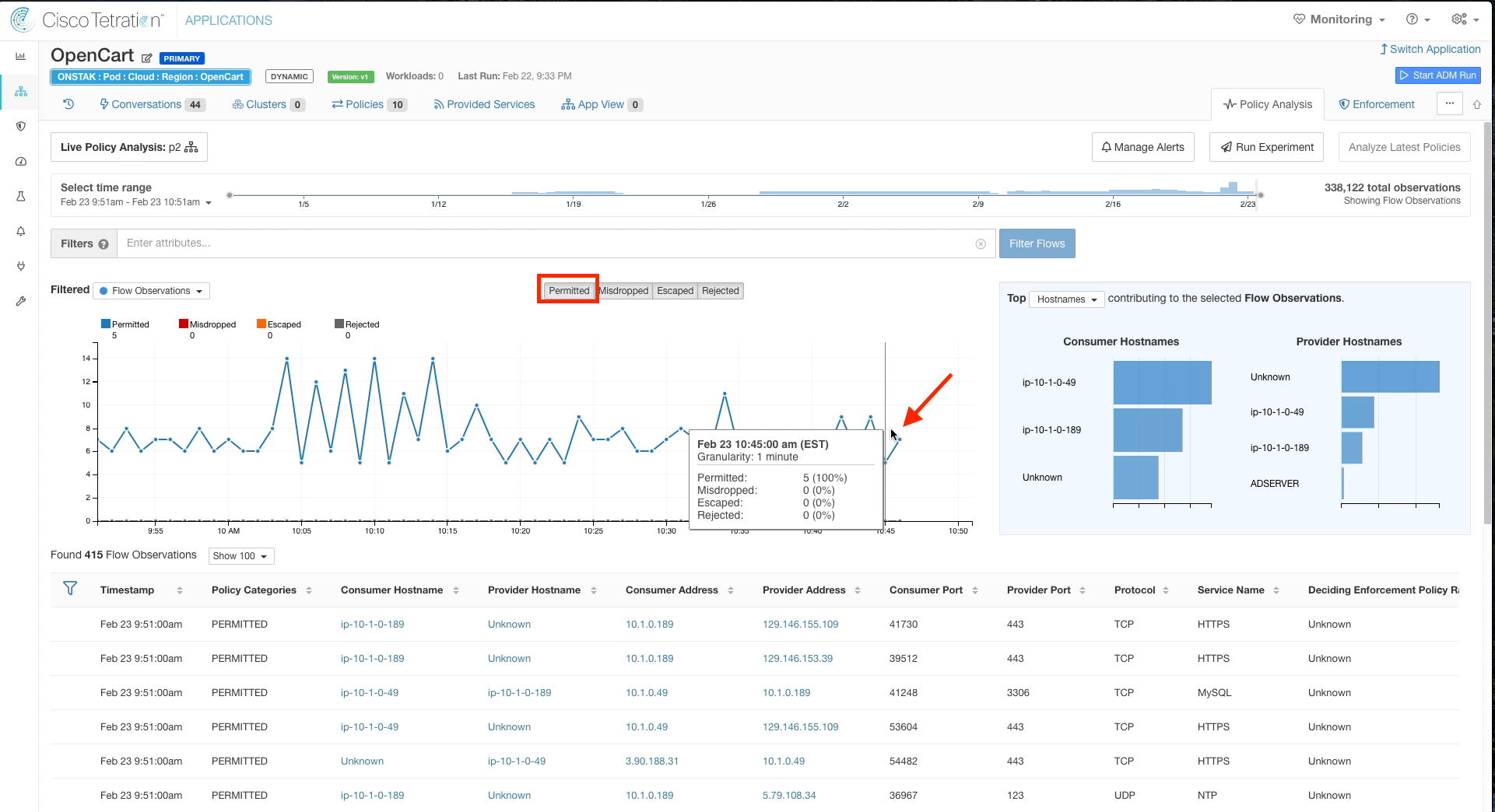
Click on a point in the graph past the time when the policy was last published. Here you should see the flows that were indicated as Escaped showing as Permitted.
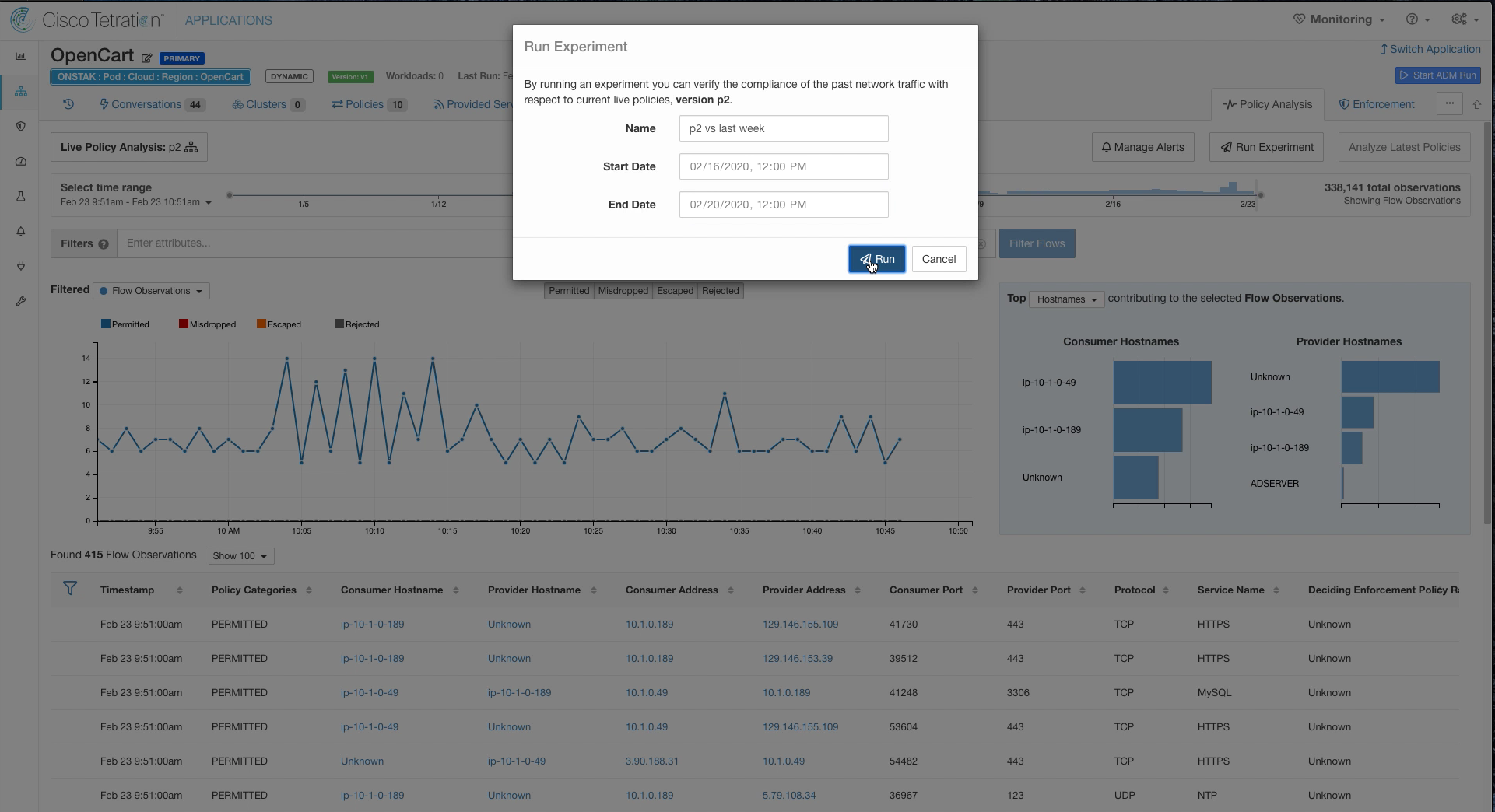
Click on Run Experiment.
An experiment allows you to compare the current policy against historical traffic. It helps you answer the question, what would have happened to the historical flows if the current policy was applied.
Select the last 24 hours for Start Date and End Date, and then select Run.
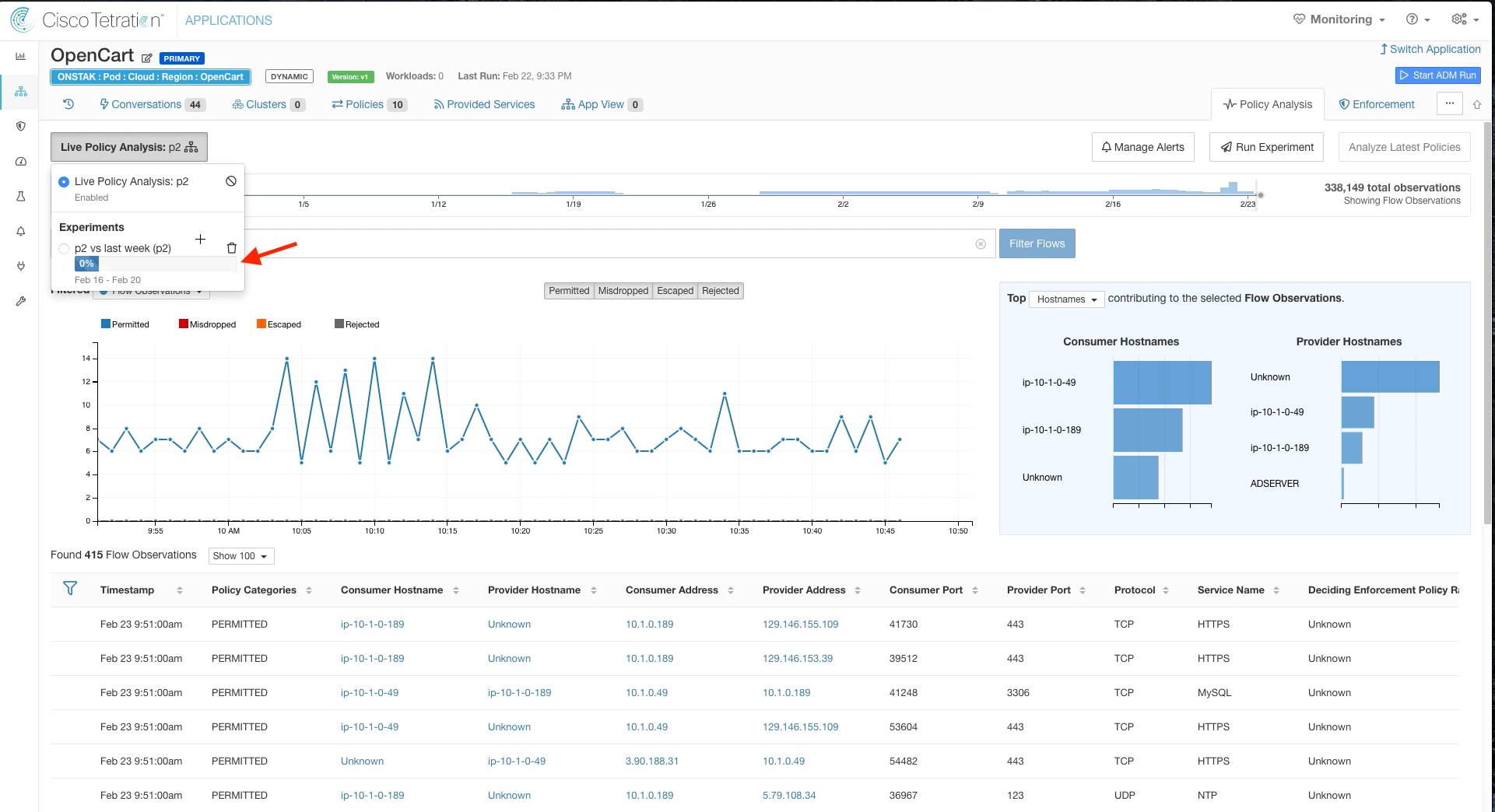
The experiment will take a few minutes to complete.
Click on Live Policy Analysis to view the status of the experiment.
Once the experiment is complete, click on it to view the results.
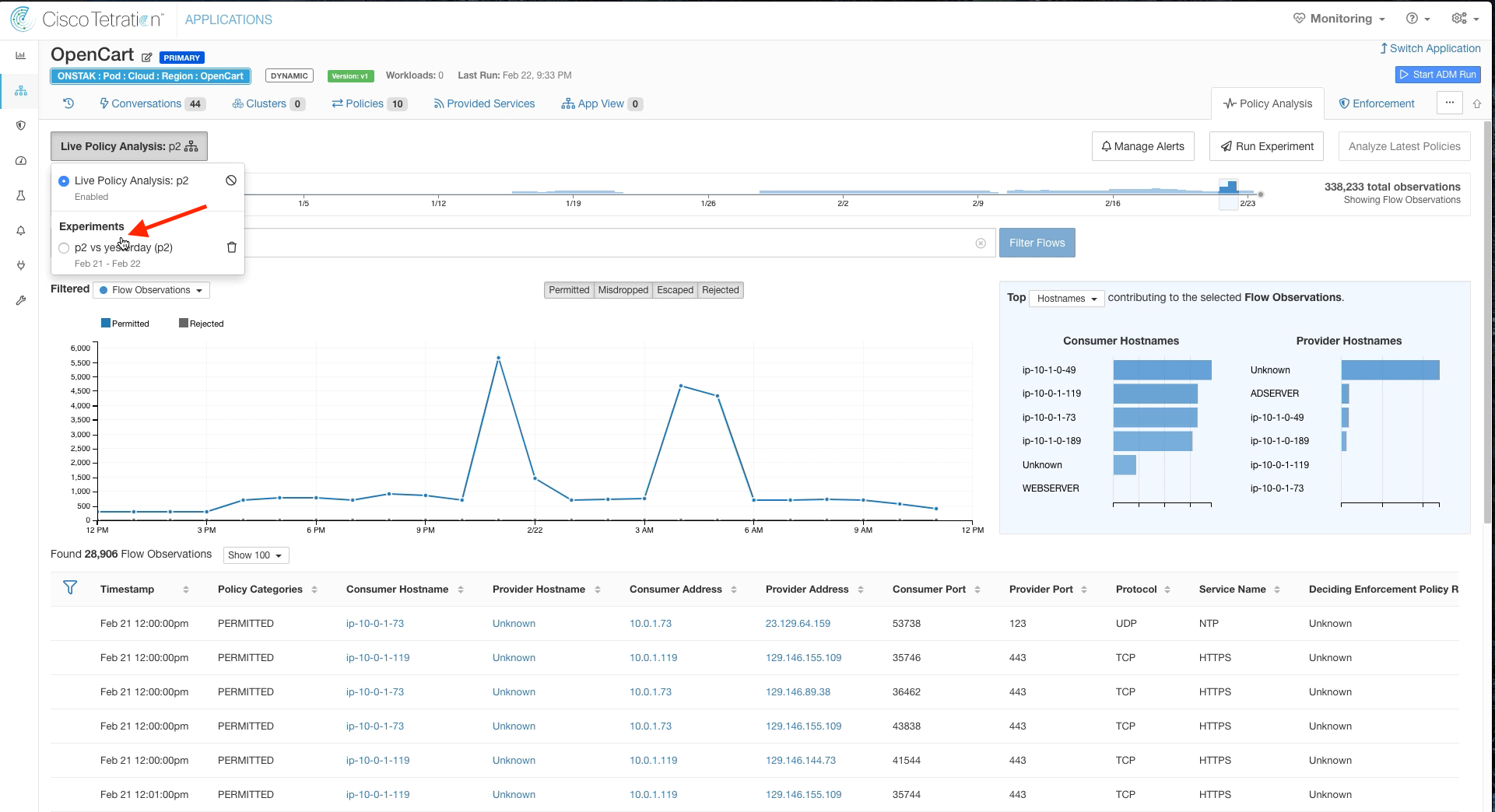
Filter oput Permitted flows.
Notice that there are some rejected flows to TCP port 8080.
Click on the flow to TCP port 8080 and select Quick Policy Analysis.
The Policy Decision is deny. This is the desired outcome for this traffic because it will block the attacker from coming in on that port to the Apache Struts application.
YOU HAVE FINISHED THIS MODULE
| Return to Table of Contents | Go to Top of the Page | Continue to the Next Module |